
TOP STORY
Dec 19, 2024
Zero trust architecture isn't rocket science. But, as in rocket science, stripping away unnecessary functions and streamlining existing ones is a step in the direction of simpler, more elegant solutions.
“Any intelligent fool can make things bigger and more complex. It takes a touch of genius – and a lot of courage – to move in the opposite direction.” -Albert Einstein
Last October, SpaceX made history by successfully catching its Super Heavy rocket in a pair of robotic arms known as “chopsticks.” This seminal achievement, seen as a major step toward making spaceflight more economically feasible and repeatable, was made possible not by adding complexity to the most advanced rockets the world has ever seen, but by stripping it away. CISOs should take note.
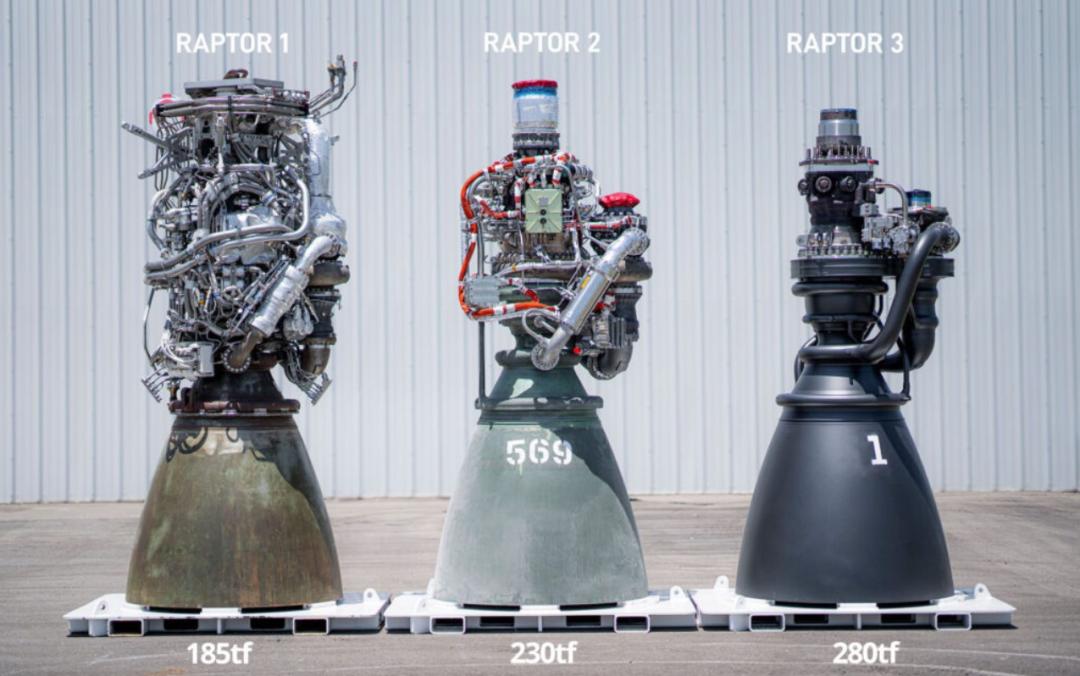
This workhorse powering this achievement was SpaceX’s third-generation Raptor engine. As you may have seen, Raptor 3 sports a far cleaner look than its predecessors. By using new techniques and reconsidering the need for exposed metal hardware and a heat shield, the engine weighs significantly less than earlier models, leading to 50% more thrust and 25% less weight. The streamlined design may also enhance the lifespan and “manufacturability” of the engines.
Complexity is the enemy of security
SpaceX was able to achieve the once-unthinkable not by adding components (and complexity) to the design of its engines, but by eliminating and optimizing existing ones. Further, Lusser's Law tells us the failure rate for complex systems can be described as the product of each component’s probability of failure. Reducing the number of components in a system can reduce the risk of failure.
SpaceX and Lusser’s Law should cause CISOs to reevaluate how we think about our IT environments. Consider the many components that make up legacy network security architecture – firewalls, SWGs, load balancers, DDoS mitigation, VDI, VPN, DLP – often in multiple instances per inbound/outbound DMZ.
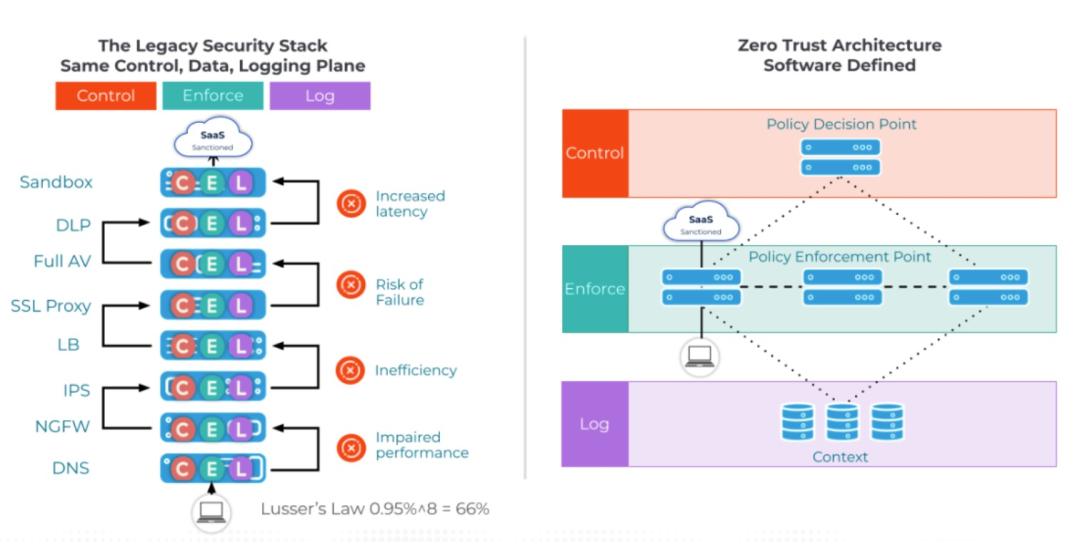
Each of these tools has a failure rate, and the failure rate of the complete system itself is higher than of each individual component. Note that “failure,” in this example could have many faces. It could take the form of a CVE, latency, inefficiency, impaired performance, defect, end-of-life – the list is as long as our imaginations allow.
Now, add to this the fact that many security executives have inherited these tools without a complete understanding of how they actually secure their environments – another lock on the safe is always welcome added protection, right?
Not so fast. It may, in fact, be just another point of failure vulnerable to any cybercriminal who happens to have studied its weaknesses. More devices and a larger attack surface means more options for attackers.
Decoupling security from the network
Zero trust is an approach that de-emphasizes perimeter-based protection – and all of its requisite outbound and inbound DMZ point products – in favor of per-resource policy enforcement when a user requests access to a company asset. When conducted in the cloud, all of the benefits of any other SASE applications to cybersecurity. This includes a vendor’s ability to specialize in its core value proposition, a reduced reliance on manual procedures from clients, and a “cloud effect” of protection from known vulnerabilities. Single-scan, multi-action (SSMA) architecture means they happen more efficiently than service-chaining multiple point products.
Importantly, true zero trust can not be a lift-and-shift of previous security capabilities to the cloud. Firewall and VPN vendors have tried these moves before and, in addition to their ability to be discovered and probed for weaknesses from the internet, they have shown to be plagued by the same vulnerabilities affecting other security appliances. Various vendor-specific zero day threats continue to add risk and cause disruption regardless of whether the underlying capabilities are hardware or cloud-based.
.png)
True zero trust architecture decouples security functions from the network, turning the network into simply the "plumbing" responsible for moving packets as quickly and reliably as possible. This means companies need only focus on these two main goals – speed and efficiency – at the network level.
Traditional security DMZ functions can then be processed in parallel (SSMA) without the need for service chaining. Connection info is shared into memory where multiple, parallel engines apply policy checks to the data. The benefit of not being a checkpost in the network, but feeding context from users and workloads provides the ability to build simple business policies, rather than complex network policies.
Zero trust architecture isn't rocket science. But, as in rocket science, stripping away unnecessary functions and streamlining existing ones is a step in the direction of simpler, more elegant solutions. So don’t be afraid to aim high.
Recommended
