
TOP STORY
CXO Monthly Roundup, February 2025: DeepSeek impersonators, Xloader evasion techniques, and Linkc ransomware group
Mar 14, 2025
Zscaler ThreatLabz analyzed fraudsters impersonating DeepSeek, examined strategies used by Xloader versions 6 and 7, and uncovered Linkc, a new ransomware group.
Welcome to the new CXO Monthly Roundup, an expansion from "CISO" due to the interest in this ongoing series from all technical C-level readers. We feature the latest threat research from the Zscaler ThreatLabz team, along with other cyber-related insights.
Over the past month, we’ve analyzed fraudulent websites designed to impersonate DeepSeek and mislead unsuspecting users into divulging sensitive information and executing harmful malware, examined network communication strategies used by Xloader version 6 and 7, and uncovered Linkc, a new ransomware group that has launched a data-leak site.
DeepSeek Lure Using CAPTCHAs to Spread Malware
In my January roundup, I mentioned how DeepSeek was making waves around the world. Generative AI tools, in general, are extremely popular right now. The international buzz around DeepSeek has led me to reflect on the security implications organizations must consider as more DeepSeek-like generative AI models emerge.
Beyond the risks of empowering otherwise low-skill cybercriminals and enabling data exfiltration, we’ve observed another interesting trend: threat actors are capitalizing on the popularity of generative AI tools by using look-alike domains to trick users into downloading malware.
In a recent blog post, ThreatLabz analyzed a malware campaign leveraging the popularity of the DeepSeek name. In addition to brand impersonation, this attack chain employs techniques such as clipboard injection to deliver malicious PowerShell commands, the deployment of the Vidar information stealer, and the abuse of legitimate platforms like Telegram and Steam to mask command-and-control (C2) communication.
The campaign starts with attackers setting up a fake domain designed to impersonate DeepSeek. Visitors to the site are prompted to complete a registration process, which redirects them to a fake CAPTCHA page. Malicious JavaScript embedded in the page copies a harmful PowerShell command to the user's clipboard, encouraging them to execute it. If the user runs the command, a packed Vidar executable (1.exe) is downloaded and executed. Vidar then exfiltrates stolen data to the C2 server, using platforms such as Telegram and Steam to disguise its activities.
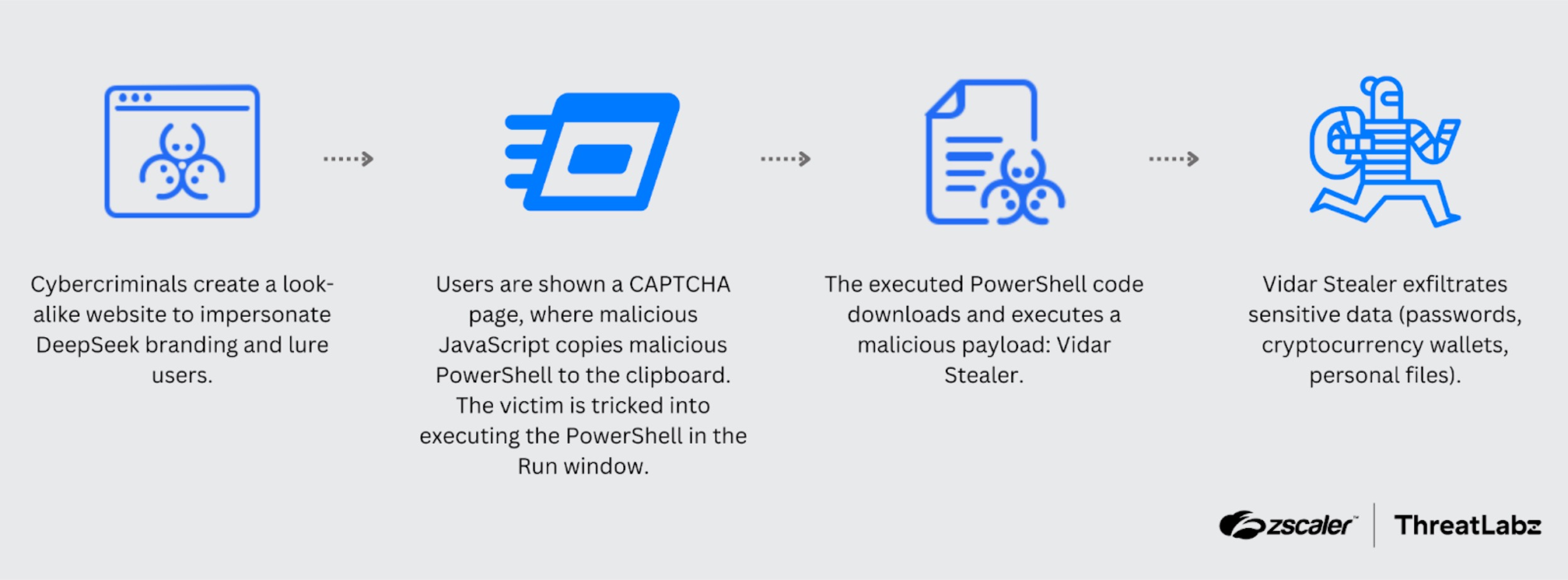
Once it infects a victim’s system, Vidar searches for files and configurations associated with major cryptocurrency wallets. It also looks for browser-related assets such as stored cookies, saved login credentials, and autofill data. The malware exfiltrates the stolen data to attacker-controlled servers using hardcoded endpoints and uses legitimate services like Telegram and Steam to relay the location of the C2 infrastructure.
Read the blog post which has a detailed list of targeted cryptowallets, browsers, filenames, and extensions, as well as additional DeepSeek-themed look-alike domains.
Zscaler Zero Trust Exchange Coverage – Zscaler Internet Access (Advanced Cloud Sandbox, Advanced Threat Protection, SSL Inspection)
New Ransomware Group "Linkc" Targets AI Company, Exposes Sensitive Data
Zscaler ThreatLabz researchers have uncovered a new ransomware group operating under the name Linkc. The group has listed an AI company on its dark web data leak site.
According to the ransom note, the group has leaked a large amount of sensitive information, including:
- Unanonymized customer datasets intended for AI model training.
- Full source code from the company’s Git repositories, including proprietary AI frameworks, GPT models, and technology for driverless systems.
- Internal documentation, contracts, project costs, and details of confidential projects.
- Backup copies of employee email accounts, containing sensitive discussions and customer correspondence.
The Linkc ransomware group claims to have exposed not only the AI company’s internal operations but also sensitive customer data, including critical datasets used for developing AI models. Such a breach could have far-reaching implications for the company’s clients and the broader AI industry, especially with the rapid adoption of generative AI tools at the enterprise level.
Ransomware groups like Linkc increasingly target organizations working with cutting-edge technologies like AI, because these companies manage vast amounts of sensitive data and intellectual property. With security protocols for generative AI tools still in their early stages, these systems present an attractive and vulnerable target for cybercriminals. Learn more about how Zscaler can help secure AI activity and data for organizations.
Zscaler Zero Trust Exchange Coverage – Zscaler Internet Access (Advanced Cloud Sandbox, Advanced Threat Protection, SSL Inspection), Zscaler Private Access (App Protection & Deception)
Technical Analysis of Xloader Versions 6 and 7 | Part 2
ThreatLabz published part 2 of the Xloader series, where we examine network communication strategies leveraged by Xloader version 6 and 7. In part 1, we analyzed Xloader’s capabilities as an information stealer and second-stage downloader. In part 2, we explore how it uses multilayered encryption techniques and fake command-and-control (C2) servers to further evade detection and hinder analysis.
One of Xloader's key obfuscation techniques involves using decoy and real C2 servers. Decoy servers are encrypted across three layers using dynamically generated keys, a process that masks malicious network traffic by blending it with legitimate-looking activity. This multilayered process is shown in the figure below.
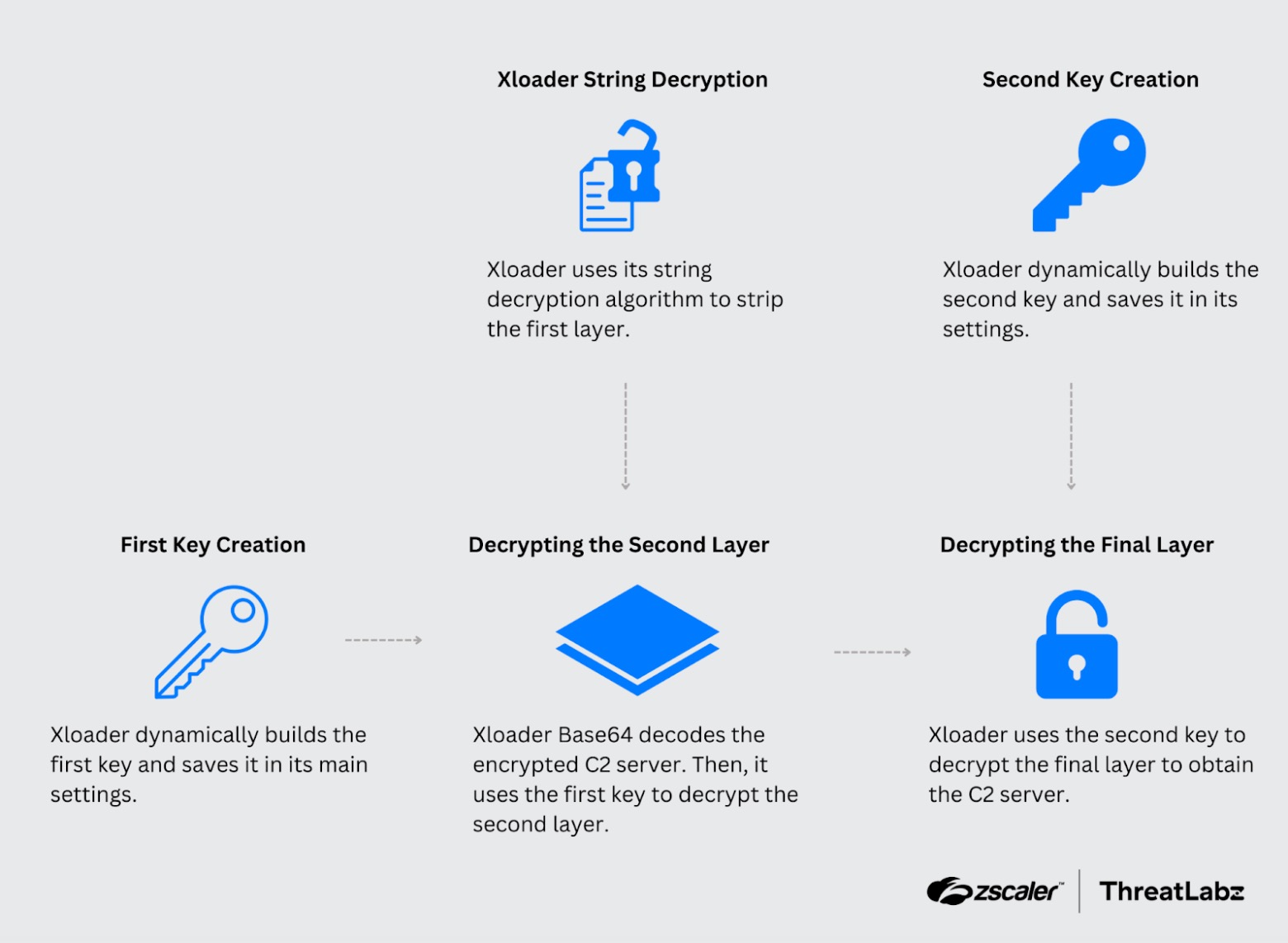
This technique mimics the behavior of benign domains and makes detection through traffic analysis challenging. The real C2 servers are encrypted differently, stored separately, and distinguished by specific characteristics such as the inclusion of “www” subdomains. In newer versions, each C2 server, including decoys, is paired with unique URL paths to further disguise malicious activity. For more details, read Technical Analysis of Xloader Versions 6 and 7 | Part 2.
Zscaler Zero Trust Exchange Coverage – Zscaler Internet Access (Advanced Cloud Sandbox, Advanced Threat Protection, SSL Inspection)
About ThreatLabz
ThreatLabz is the embedded research team at Zscaler. This global team includes security experts, researchers, and network engineers responsible for analyzing and eliminating threats across the Zscaler security cloud and investigating the global threat landscape. The team shares its research and cloud data with the industry at large to help promote a safer internet.
The Zscaler Zero Trust Exchange
Zscaler manages the world’s largest security cloud. Each day, Zscaler blocks over 150 million threats to its 7300+ customers, securing over 300 billion web transactions daily. The Zscaler ThreatLabz security research team uses state-of-the-art AI/ML and machine-learning technology to analyze Zscaler Zero Trust Exchange traffic and share its findings.
Recommended
