The CISO Monthly Roundup provides the latest threat research from the ThreatLabz team, along with CISO insights on other cyber-related subjects. Over the past month we analyzed the Steal-It campaign, HijackLoader, and APT36’s updated arsenal. We also examined a rise in tech-support scams, generative AI trends, and ransomware attacks on the gaming industry.
Steal-It Campaign
Zscaler ThreatLabz recently uncovered a new cyber campaign we’ve named “Steal-It”. In this operation, threat actors employ customized versions of the Nishang Start-CaptureServer PowerShell script to pilfer NTLMv2 hashes and execute various system commands. The stolen data is exfiltrated using Mockbin APIs. A noteworthy aspect of this campaign is its geofencing strategy, focusing primarily on targeting regions like Australia, Poland, and Belgium. To infiltrate systems, the threat actors distribute LNK files concealed within zip archives, ensuring persistence through strategic utilization of the StartUp folder. The campaign’s tactics and similarities suggest a possible link to APT28, also known as Fancy Bear, as reported by CERT-UA.
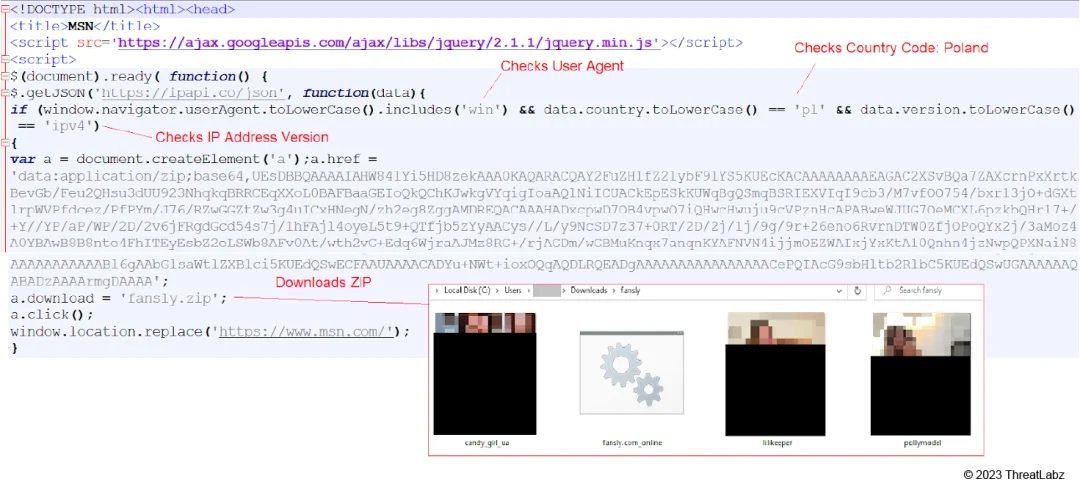
The key takeaways from this discovery include the threat actor’s use of customized Nishang scripts for stealing and exfiltrating NTLM hashes and system information through scripted command execution, with data transferred via mock APIs. Additionally, the campaign uses explicit images of models to lure victims into executing the initial payload.
Zscaler Zero Trust Exchange Coverage - Advanced Cloud Sandbox, Advanced Threat Protection, Advanced Cloud Firewall, SSL Inspection.
Rise in Tech-Support Scams Abusing Windows Action Center Notifications
The Zscaler ThreatLabz team has recently detected a surge in tech-support scams characterized by a shift toward using Windows Action Center notifications to present deceptive warning messages to users. In contrast to previous scams that primarily impersonated Windows Defender, these scammers have expanded their tactics to mimic other security providers like McAfee and Avast. The modus operandi now involves redirecting users to fraudulent tech-support pages through pirated movie streaming websites and scam tweets using fake profiles on X (formerly Twitter), leveraging Windows Action Center notifications to display fictitious warnings and alerts.
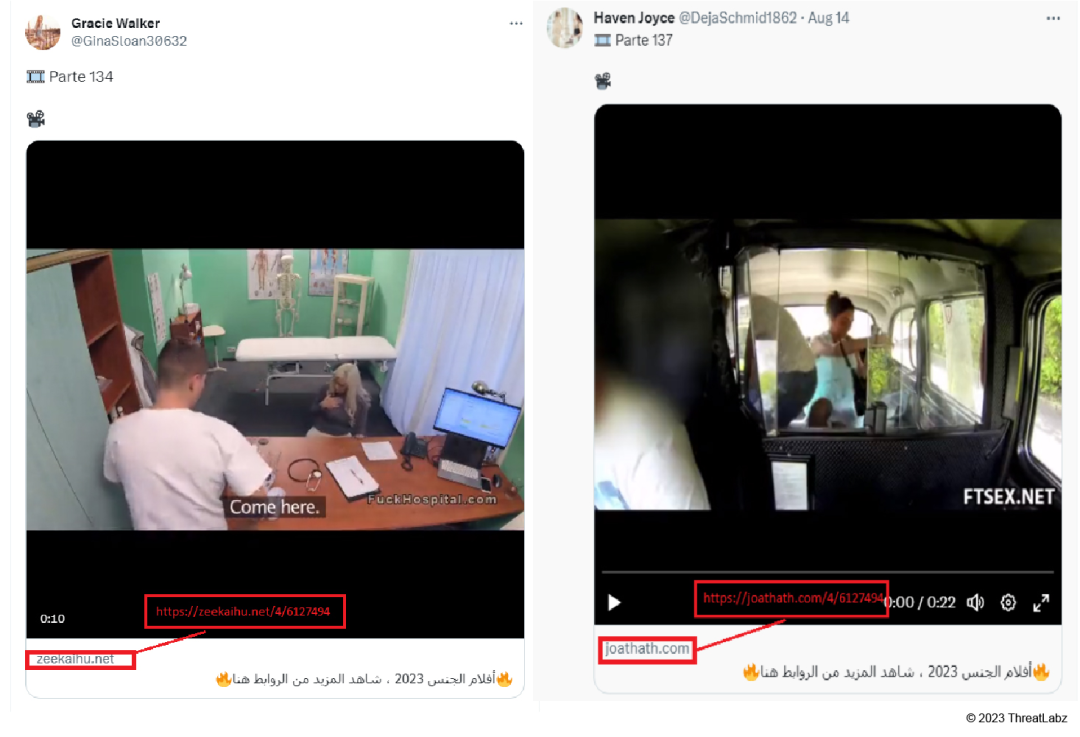
Our analysis dives into two specific tech-support campaigns, shedding light on their strategies to deceive users into accepting fraudulent notifications, subsequently inundating them with counterfeit infection-related warnings. This campaign primarily targets users in Australia, Canada, Japan, and the United States.
Zscaler Zero Trust Exchange Coverage - Advanced Cloud Sandbox, Advanced Threat Protection, Advanced Cloud Firewall, SSL Inspection.
Technical Analysis of HijackLoader
Hijackloader, a recently discovered malware loader, has gained popularity in recent months due to its modular architecture, which allows it to utilize various modules for code injection and execution. Despite its lack of advanced features, it has been observed loading different malware families like Danabot, SystemBC, and RedLine Stealer.

In our technical analysis, we examine HijackLoader’s inner workings, including its initialization, modular design, and anti-analysis techniques. Notably, it was first spotted by ThreatLabz in July 2023. HijackLoader poses an increased threat due to its ability to deliver multiple malware strains while employing syscalls to evade security monitoring. It also uses flexible code injection through embedded modules, a feature uncommon among traditional loaders.
Learn more by going to our full technical analysis
Zscaler Zero Trust Exchange Coverage - Advanced Cloud Sandbox, Advanced Threat Protection, Advanced Cloud Firewall, SSL Inspection.
A peek into APT36’s updated arsenal
In July, Zscaler ThreatLabz discovered a new wave of malicious activity orchestrated by APT36, a Pakistan-based advanced persistent threat group known for conducting targeted espionage operations in South Asia. This latest campaign saw APT36 targeting Indian government sectors, utilizing a previously undocumented Windows RAT, fresh cyber espionage utilities for Linux, novel distribution methods, and a new attack vector for Linux.

In our report, we dive into the group’s updated arsenal, featuring:
- A custom Windows RAT, dubbed ElizaRAT, that establishes C2 communication via Telegram
- Abuse of legitimate services like Google Drive and Telegram
- An innovative weaponization of Linux desktop configuration files for new attack vectors
- Careful concealment of any connections to the threat actor origin, often employing the same C2 infrastructure for various malicious activities
Read our comprehensive report here
Zscaler Zero Trust Exchange Coverage - Advanced Cloud Sandbox, Advanced Threat Protection, Advanced Cloud Firewall, SSL Inspection.
Ransomware Attacks on Gaming Industry - A CISO Perspective
In this blog, I give my perspective on the recent ransomware attacks impacting the gaming industry. Specifically, I examine activity from UNC3944, an affiliate of the BlackCat threat group, and their role in the attacks on the gaming industry. These attacks come after international law enforcement agencies shut down two of the largest initial access brokers (IAB), Emotet and Qakbot. The fall of these two IABs has reduced attacks leveraging malicious email attachments and links and is forcing threat actors like UNC3944 to adopt alternative techniques.
The UNC3944 attacks against the gaming industry utilize three major threat trends we commonly see in our research. Specifically:
- Social engineering: UNC3944 frequently leverages social engineering tactics including vishing [voice-phishing], in order to compromise systems. Many of their recent attacks involve using social engineering to steal credentials and gain access to systems without triggering security controls.
- Ransomware-as-a-service: Ransomware-as-a-Service (RaaS) allows threat actors to scale their profits and operations. It lets ransomware groups outsource the infiltration, lateral movement, data theft, and deployment of their ransomware payload in exchange for a commission.
- Double extortion: Threat actors are finding it profitable to encrypt data on the victims’ systems and then exfiltrate it for further leverage. If victims are reluctant to pay the ransom, adversaries threaten to publicly publish the stolen data.

In the blog, I examine UNC3944’s known attack vectors and examine some commonalities between the tactics used by ransomware groups. Once you see the sequence threat actors use to deploy ransomware, it becomes easier to understand how zero trust solutions disrupt the attack chain.
UNC3944 teamed up with BlackCat as an affiliate in the latest attacks on the gaming industry. While law enforcement has dealt a blow to other IAB malware groups, UNC3944 is successfully using techniques such as SIM swapping scams, multi-factor authentication fatigue, and smishing (SMS phishing). They are also using voice-over-phone phishing, or vishing, to trick targets into helping them gain unauthorized access. Vishing is a technique that can greatly benefit from using AI, and may soon become a staple in threat actor’s toolkits.
To learn more about the ransomware threat landscape and the recent attacks, view my on-demand webinar here: https://info.zscaler.com/webinar-ransomware-threat-update-defend-against-the-latest-attack-trends
Gain insight by reading the rest of this blog
Analysis of Generative AI Trends and ChatGPT Usage
The release of ChatGPT highlights the potential for artificial intelligence (AI) and machine learning (ML) to reshape how organizations operate. Large Language Models (LLMs), driven by extensive datasets, play a key role in transforming user interactions. Our analysis offers insight into AI’s impact and provides guidelines for responsible AI integration.
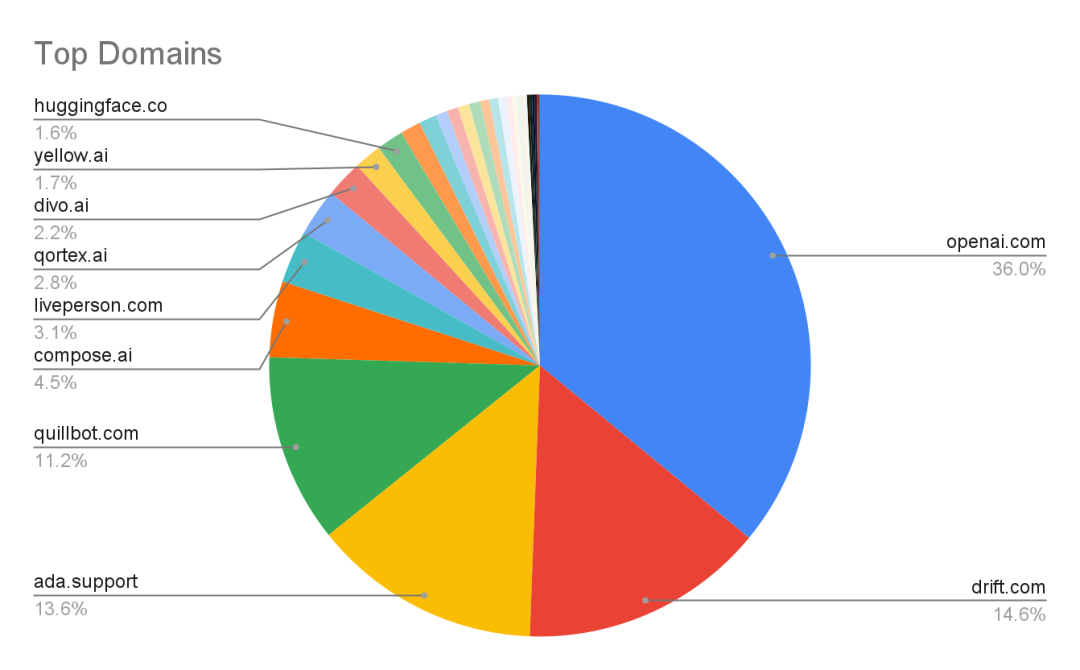
Our team found that OpenAI.com is a hub for AI enthusiasts, with ChatGPT driving over half of its traffic. Drift excels in language processing and rivals ChatGPT’s popularity. While ChatGPT saw a surge in usage earlier this year, it plateaued in August. The majority of AI/ML traffic originates from the United States and India, with generative AI as the primary use case.
About ThreatLabz
ThreatLabz is the embedded research team at Zscaler. This global team includes security experts, researchers, and network engineers responsible for analyzing and eliminating threats across the Zscaler security cloud and investigating the global threat landscape. The team shares its research and cloud data with the industry at large to help promote a safer internet.
The Zscaler Zero Trust Exchange
Zscaler manages the world’s largest security cloud. Each day, Zscaler blocks over 150 million threats to its 7300+ customers, securing over 300 billion web transactions daily. The Zscaler ThreatLabz security research team uses state-of-the-art AI/ML and machine-learning technology to analyze Zscaler Zero Trust Exchange traffic and share its findings.
What to read next:
Why your public partners care about your cybersecurity approach
Human discretion is great, right? Not when it’s the lifeblood of social engineering attacks

