The CISO Monthly Roundup provides the latest threat research from the ThreatLabz team, along with CISO insights on other cyber-related subjects. This edition contains analysis of ValleyRAT, SmokeLoader, and cyberattack by the threat group Kimsuky. It also has a recap of my Zenith Live ‘24 keynote and updates on prevalent ransomware activity.
Technical analysis of the latest variant of ValleyRAT
Zscaler ThreatLabz recently identified a new campaign delivering the latest version of ValleyRAT, a remote access trojan (RAT) first documented in early 2023. The delivery occurs in multiple stages through phishing emails and malicious downloads. In this latest campaign, ValleyRAT demonstrated new commands, such as capturing screenshots and forcing shutdowns.
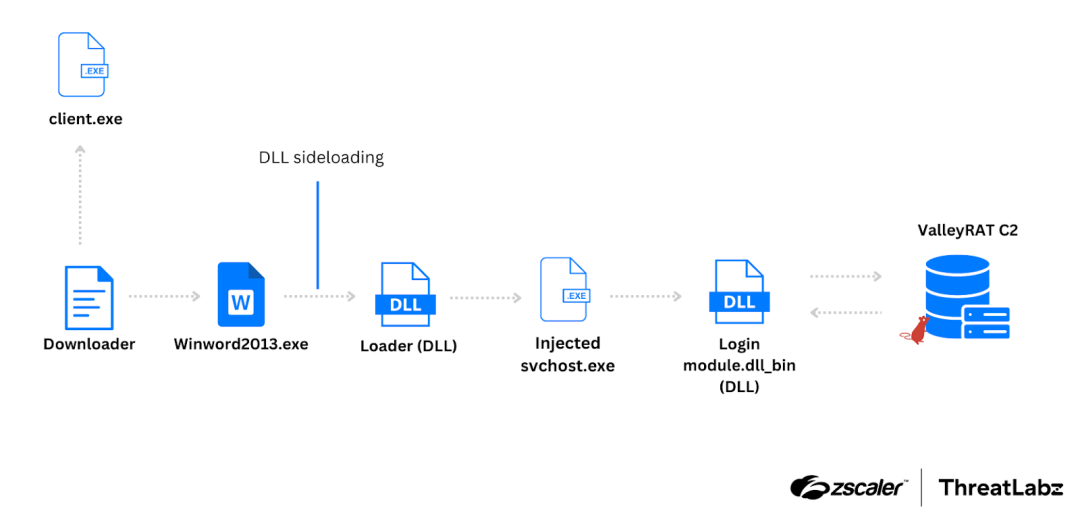
The initial stage downloader utilizes an HTTP File Server (HFS) to obtain files required for subsequent stages. The downloader and loader employ various evasion techniques such as anti-virus checks, DLL sideloading, and process injection. The ValleyRAT sample we examined had modifications in its device fingerprinting, bot ID generation, configuration format, and supported commands. This malware continues to be actively developed and updated, making it a prevalent threat that should be watched by organizations.
Zscaler Zero Trust Exchange Coverage - Advanced Cloud Sandbox, Advanced Threat Protection, Advanced Cloud Firewall, SSL Inspection.
A brief history of SmokeLoader, part 1
Zscaler ThreatLabz conducted a technical analysis of SmokeLoader in May 2024 that contributed to Operation Endgame, an international law enforcement action that successfully eliminated tens of thousands of infections. In this blog of a two-part blog series, we explore the evolution of SmokeLoader. Initially used as a first-stage downloader to deploy other malware families, SmokeLoader has evolved to include its own framework and expand its capabilities with information stealing functionalities. A Brief History of SmokeLoader, Part 1 provides a timeline of SmokeLoader's evolution from 2011 to 2022. It focuses on the versions from 2011-2013 and the ancient modularizations in 2014. We also examine the anti-analysis techniques and persistence mechanisms employed by SmokeLoader, as well as its communication protocol.
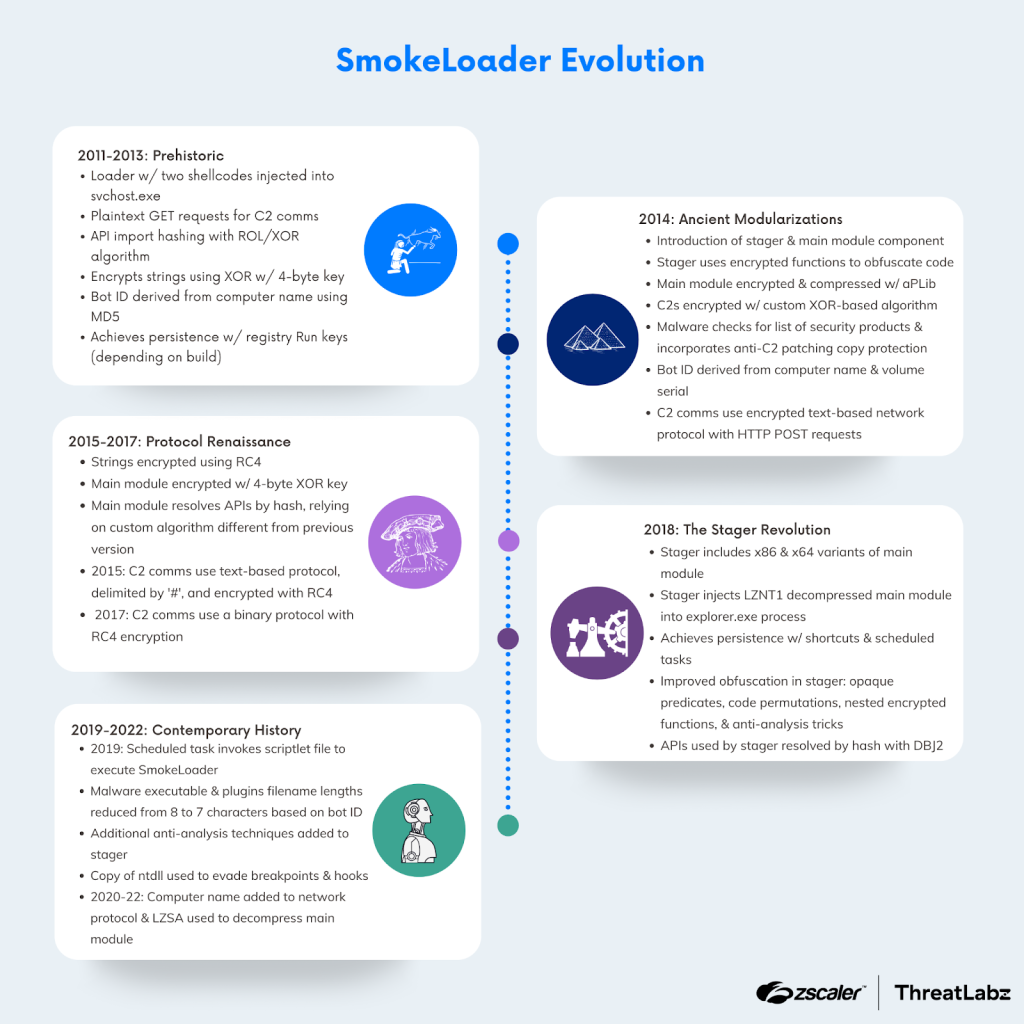
When SmokeLoader emerged its main purpose was to function as a downloader and facilitate the execution of second-stage malware. However, SmokeLoader's capabilities extend beyond mere downloading, as it has the ability to acquire additional modules that enhance its functionalities. These additional modules enable SmokeLoader to engage in various malicious activities such as data theft, distributed denial of service (DDoS) attacks, and cryptocurrency mining. To evade detection, SmokeLoader employs tactics like identifying analysis environments, generating fake network traffic, and obfuscating its code. Throughout its existence, SmokeLoader has undergone extensive development, introducing new features and implementing improved encryption, compression, and hash algorithms.
Zscaler Zero Trust Exchange Coverage - Advanced Cloud Sandbox, Advanced Threat Protection, Advanced Cloud Firewall, SSL Inspection.
Kimsuky deploys TRANSLATEXT to target South Korean academia
Zscaler ThreatLabz published an analysis of new activity from the North Korean-backed advanced persistent threat group, Kimsuky. This group is known for cyber espionage and financially motivated cyber attacks, primarily targeting South Korean entities. They have traditionally used malicious Google Chrome extensions (an example infection chain is shown in the figure below)
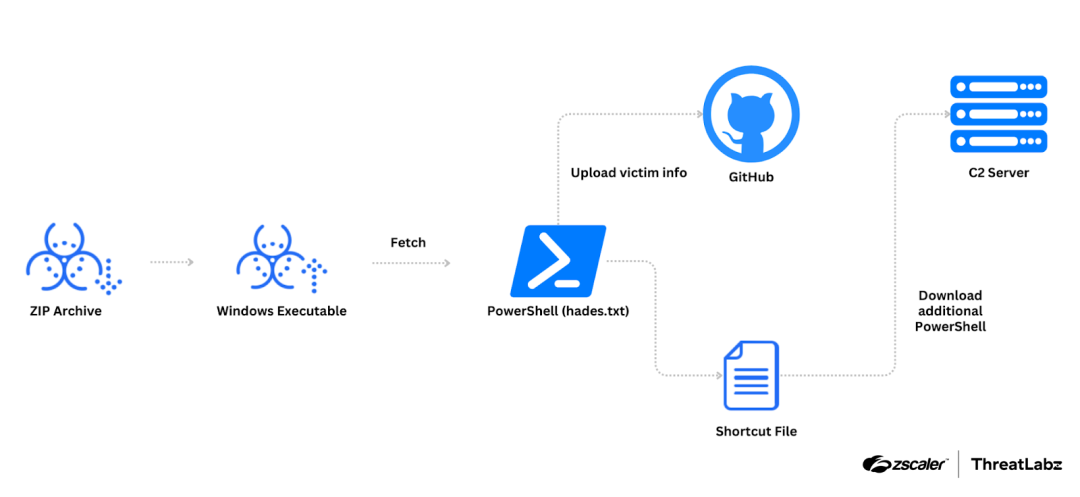
Zscaler recently observed a new extension called TRANSLATEXT being used for cyber espionage. TRANSLATEXT is designed to steal email addresses, usernames, passwords, cookies, and capture browser screenshots. The main targets of this attack are individuals involved in political research related to North Korean affairs in the South Korean academic field.
The attack involves the delivery of an archive file containing decoy files and a PowerShell script. These assets retrieve additional scripts and register the TRANSLATEXT extension in Chrome. The TRANSLATEXT extension masquerades as a Google Translate extension but contains malicious JavaScript files for stealing information and communicating with a command and control server. The stolen information is sent via HTTP POST requests. The figure below shows the relationship between the four different malicious Javascript files and how they exfiltrate data to the C2 server.
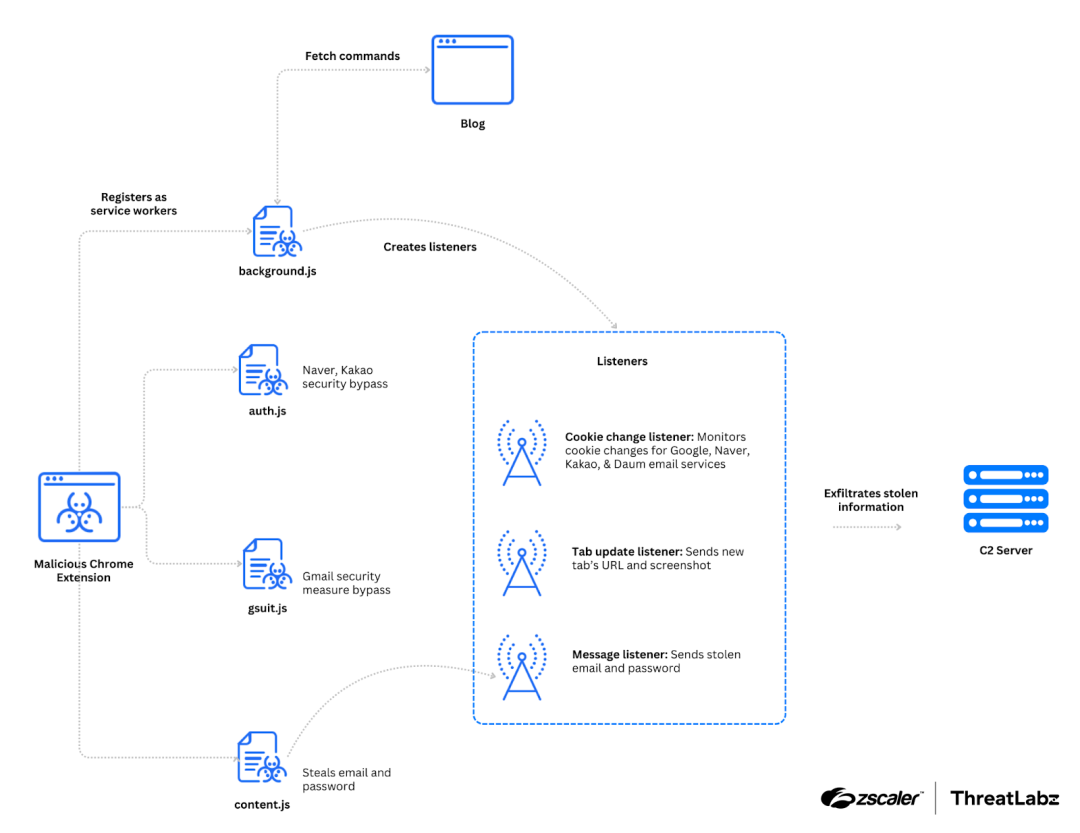
Zscaler attributes this attack to the Kimsuky group based on C2 server characteristics and target selection. The group has a history of using the b374k webshell and frequently redirects connections to legitimate services like Gmail to lower suspicion. The group also used the domain "r-e.kr" to host the malicious PowerShell scripts, which is a domain they have used in the past.
Zscaler Zero Trust Exchange Coverage - Advanced Cloud Sandbox, Advanced Threat Protection, Advanced Cloud Firewall, SSL Inspection.
Recap of Zenith Live cyber and AI innovation keynote
During Zenith Live ‘24 I had the honor of sharing the stage with Stephen Harrison, MGM Resorts SVP & CISO, and Eric Reed, Cigna Group CTO. We presented a cyber and AI innovation keynote in Las Vegas, engaging with security and technology experts from leading global organizations. Their insights on innovation and leading the change in the era of GenAI driven attacks were truly valuable. We discussed the importance of embracing an AI-powered Zero Trust platform to fight AI-driven attacks. We also looked at why prioritizing Zero Trust Architecture is key for reducing your attack surface and shutting down threat vectors.

You can watch a video of the keynote here.
Ransomware updates
This is a new section I am adding for sharing quick updates aimed to keep the CXO & security research community informed, assist in analysis, and stay ahead in the fight against ransomware threats.
The truth behind LockBit's headlines: Bank's data leaked, not the Federal Reserve's - LockBit, a notorious cybercriminal group, recently made headlines by claiming to have leaked data from the Federal Reserve. However, upon closer examination, it became evident that the leaked data actually originated from a different source - a bank that had recently faced penalties from the Federal Reserve due to shortcomings in its anti-money laundering, risk management, and consumer compliance programs. This misleading information spread by LockBit can be seen as a clickbait tactic aimed at garnering attention from the public.
Brain Cipher, a new ransomware group emerges - We observed a new ransomware group calling themselves Brain Cipher and were able to capture their ransom note.
Latrodectus returns from the dead - The initial access broker using Latrodectus is back. The group has resurrected the malware loader less than a month after Operation Endgame. BruteRatel is currently being used to drop Latrodectus.
Black Basta ransomware group unveils updated ransom note after 2-year hiatus - After more than 2 years, the Black Basta ransomware group has updated their ransom note. The updated version of this ransom note can be seen here.
INC ransomware group upgrades payment and data leak sites - The INC ransomware group has been actively updating their payment and data leak sites. Their latest ransom note, which now includes a web-based data leak site accessible without TOR, is available on the ThreatLabz GitHub archive. View it and dozens of other ransom notes from known threat groups. These assets are provided to help your organization with detection and analysis.
About ThreatLabz
ThreatLabz is the embedded research team at Zscaler. This global team includes security experts, researchers, and network engineers responsible for analyzing and eliminating threats across the Zscaler security cloud and investigating the global threat landscape. The team shares its research and cloud data with the industry at large to help promote a safer internet. See our latest updates at www.threatlabz.com.
The Zscaler Zero Trust Exchange
Zscaler manages the world’s largest security cloud. Each day, Zscaler blocks over 150 million threats to its 7300+ customers, securing over 300 billion web transactions daily. The Zscaler ThreatLabz security research team uses state-of-the-art AI/ML and machine-learning technology to analyze Zscaler Zero Trust Exchange traffic and share its findings.
What to read next:
The unique yet familiar state of cybersecurity in ANZ
The power of breach prediction
Lean and mean: Cutting cybersecurity costs without cutting corners


