
EDITOR'S PICK
CISO Monthly Roundup, July 2024: ThreatLabz Ransomware Report, SmokeLoader, Dodgebox & MoonWalk, plus lessons from the CrowdStrike outage
Aug 19, 2024
In this edition, get an update on the ransomware threat landscape, a look at the chronology of key events for SmokeLoader, a technical breakdown of DodgeBox and MoonWalk, and lessons from the CrowdStrike outage.
The CISO Monthly Roundup provides the latest threat research from the ThreatLabz team, along with CISO insights on cyber-related subjects. In this edition, you’ll get an update on the ransomware threat landscape–we saw a record-breaking $75 million ransom payment, a technical breakdown of DodgeBox and MoonWalk from APT41, a look at the chronology of key events for SmokeLoader, and lessons from the CrowdStrike outage.
Zscaler ThreatLabz 2024 Ransomware Report
The Zscaler ThreatLabz team released its ThreatLabz 2024 Ransomware Report to shed light on the ransomware landscape. This comprehensive research analyzes 4.4 million ransomware attack attempts blocked by Zscaler. The report includes in-depth analysis of ransomware samples and attack data, providing valuable insights into primary targets, the most dangerous ransomware families, and the evolving tactics and demands of ransomware threat actors.

Key findings include:
1. ThreatLabz uncovered a $75 million payout to Dark Angels – the largest payment ever made in ransomware history.
ThreatLabz discovered a Fortune 50 company paid Dark Angels $75 million, higher than any publicly known amount.
The Dark Angels ransomware group targets a small number of high-value companies for large payouts. Once Dark Angels have identified and compromised a target, they selectively decide whether to encrypt the company’s files. In most cases, the group steals a vast amount of information, typically 1-10 TB. For large businesses, the group has exfiltrated between 10-50 TB of data, which can take days to weeks to transfer.
The Dark Angels ransomware group strategy of targeting only high-value companies offers several advantages. Firstly, this approach increases the likelihood of a substantial payout due to the financial resources of these targeted organizations. Secondly, by focusing on a single company rather than indiscriminately targeting hundreds of companies like other threat actors, Dark Angels can reduce the chances of attracting significant media attention. This allows them to potentially operate under the radar and maintain a lower profile in the news.
ThreatLabz predicts that other ransomware groups will take note of Dark Angels’ success and may adopt similar tactics.
2. The most dangerous ransomware families to monitor in 2024-2025
- Dark Angels
- LockBit
- BlackCat
- Akira
- Black Basta
Download the ThreatLabz 2024 Ransomware Report to learn why these ransomware families are considered the most dangerous.
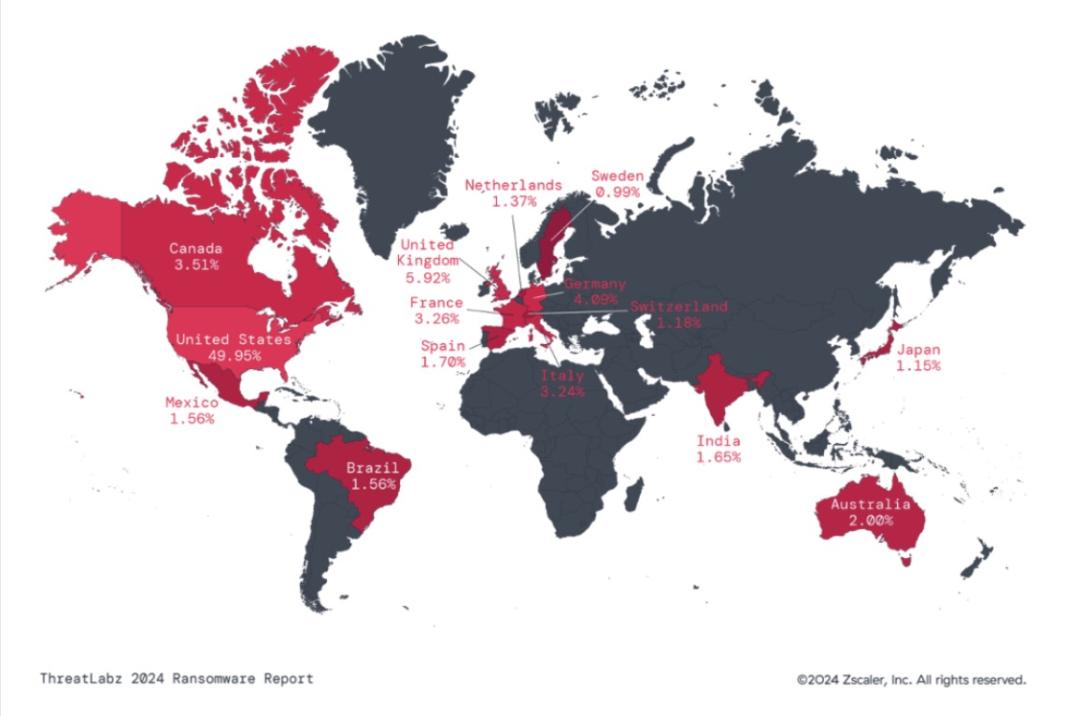
3. The US remains the top target for ransomware attacks
The United States, United Kingdom, Germany, Canada, and France were the top five countries targeted by ransomware in the same time period.
The United Kingdom is the primary target for ransomware attacks in the EMEA region, while Australia holds the top position in the APAC region.
Defending against ransomware attacks
The Zscaler ThreatLabz 2024 Ransomware Report provides essential guidance to combating ransomware, including:
- Fighting AI with AI: Learn about Zscaler’s AI-powered cyberthreat protection capabilities needed to combat AI-driven threats.
- Zero trust architecture advantages: Learn how the Zero Trust Exchange stops ransomware at every stage of the attack cycle.
- Ransomware prevention checklist: Access the latest best practices to mitigate ransomware risk and protect your organization from existing and emerging threats.
Zscaler Zero Trust Exchange Coverage - Advanced Cloud Sandbox, Advanced Threat Protection, Advanced Cloud Firewall, SSL Inspection.
DodgeBox & MoonWalk: A deep dive into the updated arsenal of APT41
This two-part blog series is a technical analysis of DodgeBox and MoonWalk. Part 1 focuses on a new malware loader called DodgeBox, which is closely linked to the China-based APT41.
DodgeBox is used to deploy a backdoor known as MoonWalk, which communicates with a C2 server via Google Drive. We identified that DodgeBox shared significant similarities with StealthVector, a tool previously associated with APT41.
DodgeBox utilizes various evasion techniques like DLL sideloading, environmental guardrails, and call stack spoofing to avoid detection. It also employs a unique method of “environment keying,” tying the payload to the specific machine it infects by re-encrypting it with the machine’s GUID.
Part 2 discusses MoonWalk, the modular malware deployed by DodgeBox. MoonWalk uses advanced evasion techniques such as DLL hollowing, import resolution, and the novel use of Windows Fibers (a rarely used Windows feature) to avoid detection by antivirus and endpoint detection and response (EDR) systems. The malware uses Google Drive for C3 communication, blending its traffic with legitimate network activity, making it difficult to detect. MoonWalk’s modular design allows for easy updates and customization, making it a highly adaptable tool for cyber espionage.

Read more about APT41 DodgeBox loader
Read more about APT41 MoonWalk backdoor
Zscaler Zero Trust Exchange Coverage - Advanced Cloud Sandbox, Advanced Threat Protection, Advanced Cloud Firewall, SSL Inspection.
SmokeLoader - A decade old downloader malware strain
When SmokeLoader first emerged in 2011, its main purpose was to function as a downloader and facilitate the execution of second-stage malware. However, SmokeLoader's capabilities extend beyond mere downloading, as it has the ability to acquire additional modules that enhance its functionalities. Over the years, SmokeLoader has incorporated the following updates:
- 2011-2013: “Prehistoric” versions of SmokeLoader malware lacked version numbers and used basic techniques to communicate with command-and-control (C2) servers. They registered with the C2 server using simple commands and employed basic anti-analysis techniques like hashed API names and encrypted strings. Despite being rudimentary, these versions laid the foundation for more advanced iterations to follow.
- 2014: SmokeLoader introduced a multi-staged loading process and split its functions into separate modules, which would go on to be a defining feature of the malware. SmokeLoader also implemented anti-analysis techniques, including checks for virtual environments, and switched to encrypted HTTP POST requests for communication.
- 2015 - 2017: SmokeLoader underwent significant changes in its communication protocol with the C2 server beginning in 2015. The network protocol was updated with fields separated by a delimiter. In 2017, SmokeLoader started using a binary protocol with encrypted requests and responses using static RC4 keys.
- 2018: SmokeLoader version 2018 introduced significant changes, particularly in the stager module, which improved obfuscation techniques and implemented anti-analysis measures. In the stager of SmokeLoader version 2018 (and newer), a majority of the code is encrypted using nested XOR layers, enhancing the encryption and obfuscation techniques employed, as shown in the figure below.
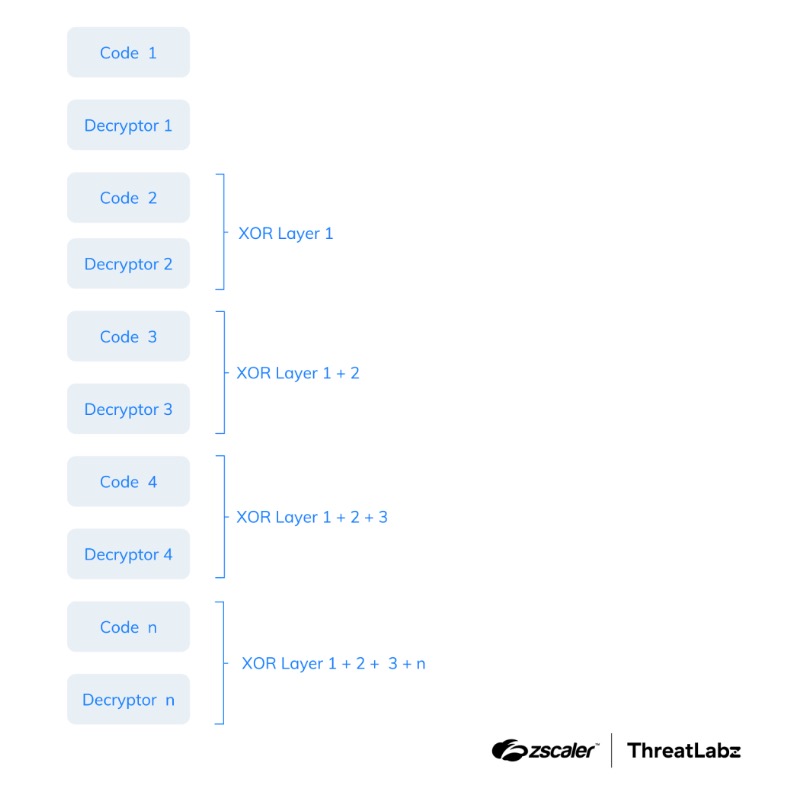
- 2019 - 2022: Recent versions of SmokeLoader have not undergone significant changes in its structure and functionality. However, there have been updates to its algorithms and anti-analysis techniques. To avoid detection, SmokeLoader's stager loads its own copy of the ntdll library into memory instead of using the default one. In versions 2020 and 2022, the malware creates this copy in memory. In the 2019 version, it creates and loads it from a copy on disk.
While the most recent known version of SmokeLoader dates back to 2022, it has been extensively deployed in numerous campaigns throughout recent years. Following Operation Endgame, there has been an overall decline in SmokeLoader activity. However, this lull will likely be short-lived as various threat actors who have leveraged SmokeLoader regroup.
Read more about SmokeLoader analysis
Zscaler Zero Trust Exchange Coverage - Advanced Cloud Sandbox, Advanced Threat Protection, Advanced Cloud Firewall, SSL Inspection.
Prevalent Threat Updates
In this new section I am adding for sharing quick updates aimed to keep the CXO & security research community informed, assist in analysis, and stay ahead in the fight against ransomware threats.
Recent CrowdStrike & Azure Outages
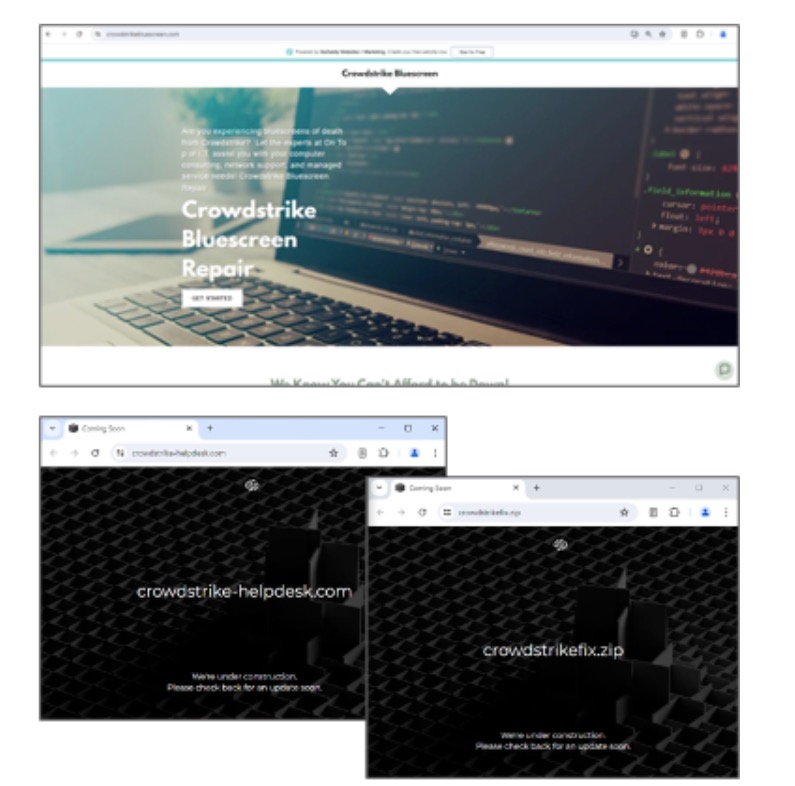
- Many of you will be familiar with the recent incidents involving CrowdStrike and Microsoft Azure that affected millions of users globally. These incidents caused major disruption for businesses and their customers, with some incurring significant costs.
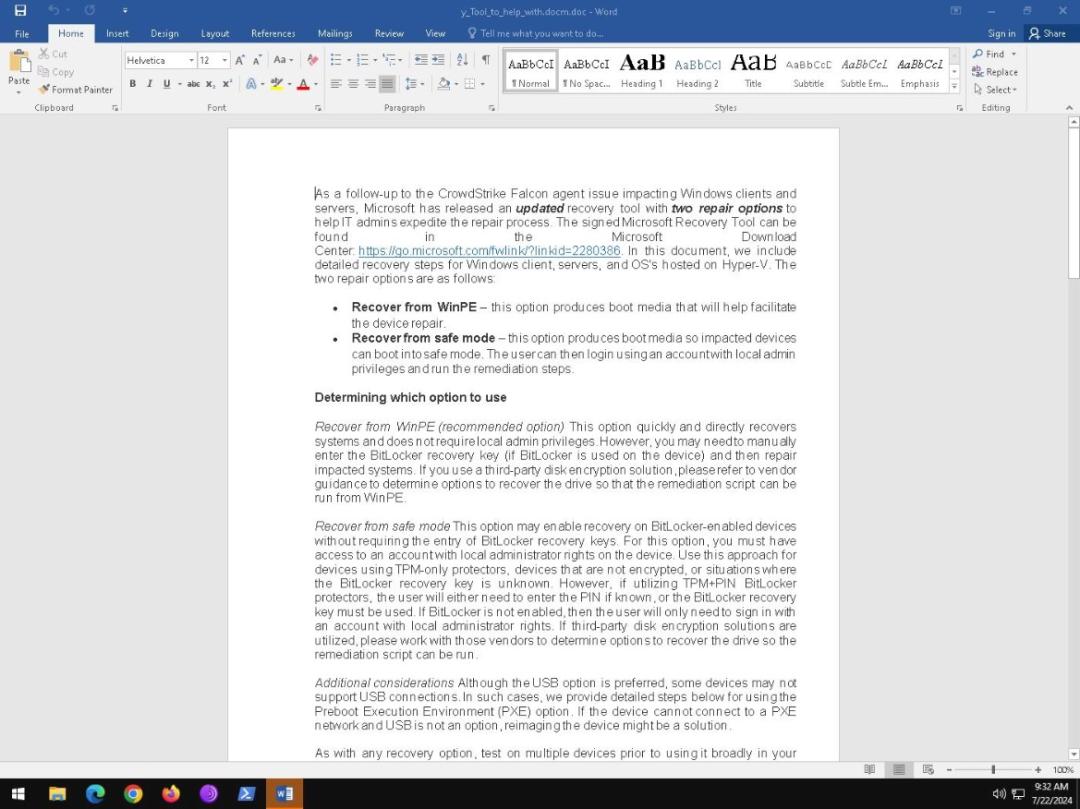
- Threat actors are exploiting the CrowdStrike BSOD bug to distribute malware via Word documents. A new lure has been identified involving a Microsoft Word document that falsely claims to offer recovery instructions. However, the document contains a malicious macro that, once enabled, downloads an information stealer from: hxxp://172.104.160[.]126:8099/payload2.txt.
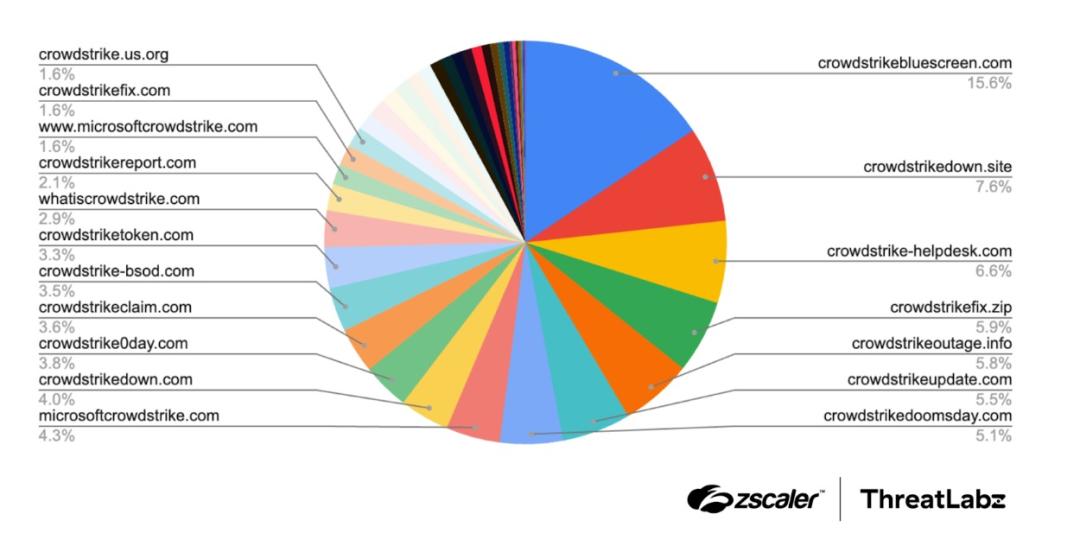
- Zscaler has discovered and blocked 230 malicious CrowdStrike look-alike domains in the first 5 days after the incident.
To hear more about preventing such outages, sign up for my upcoming webinar.
About ThreatLabz
ThreatLabz is the embedded research team at Zscaler. This global team includes security experts, researchers, and network engineers responsible for analyzing and eliminating threats across the Zscaler security cloud and investigating the global threat landscape. The team shares its research and cloud data with the industry at large to help promote a safer internet.
The Zscaler Zero Trust Exchange
Zscaler manages the world’s largest security cloud. Each day, Zscaler blocks over 150 million threats to its 7300+ customers, securing over 300 billion web transactions daily. The Zscaler ThreatLabz security research team uses state-of-the-art AI/ML and machine-learning technology to analyze Zscaler Zero Trust Exchange traffic and share its findings.
What to read next:
2023 ThreatLabz State of Ransomware report
Recommended
