
CISO Monthly Roundup, February 2024: Ivanti VPN exploits, WINELOADER attacks on European diplomats, Pikabot analysis, and Midnight Blizzard campaign
Mar 11, 2024
CISO Monthly Roundup, February 2024: Ivanti VPN exploits, WINELOADER attacks on European diplomats, Pikabot analysis, and Midnight Blizzard campaign
The CISO Monthly Roundup provides the latest threat research from the ThreatLabz team, along with CISO insights on cyber-related subjects. Over the past month we helped global organizations respond to the fallout from Ivanti VPN Zero Day exploits, investigated SPIKEDWINE campaign targeting European diplomats, delved into the details of Pikabot, and examined the Midnight Blizzard campaign.
ThreatLabz Coverage Advisory: Ivanti’s VPN Vulnerabilities Exploited by Hackers
Multiple zero-day vulnerabilities in Ivanti’s VPN products have been exploited by Chinese state-backed hackers since December 2023. Initial vulnerabilities (CVE-2023-46805 and CVE-2023-21887) allowed authentication bypass and remote command injection, with subsequent patches being bypassed through leveraging other flaws (CVE-2024-21888). The workarounds used to circumvent the initial patch allowed attackers to enable privilege escalation and perform server-side request forgery.
While the VPN exploitation activity began with nation state threat actors, they soon expanded to include several threat groups including coinminers. ThreatLabz observed adversaries deploying Monero miners as part of their attack chain, in an attempt to increase financial gains.
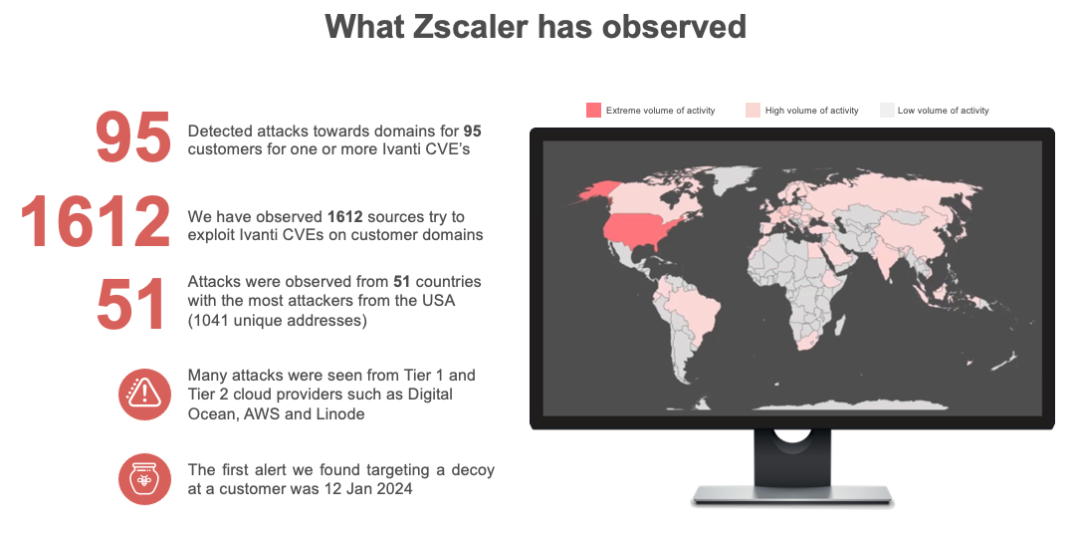
The attackers use tools like PySoxy and web shells to exploit vulnerabilities, executing a sequence of attacks involving initial exploitation, persistence, reconnaissance, credential stealing, lateral movement, and evidence wiping.

CISA has issued advisories and multiple directives urging prompt action. Their recommendations include applying patches promptly, performing factory resets, and at one point also disconnecting affected products. Zscaler recommends that organizations impacted by these VPN vulnerabilities:
- Adopt Zero Trust architecture in lieu of legacy VPN architecture to improve your security posture by not hosting users on the same network as applications (user-app segmentation).
- Prioritize segmentation of all potentially impacted systems from enterprise resources to reduce the blast radius.
- Continue threat hunting activity for all devices connected to and from the impacted Ivanti products.
- Monitor identity management services and authentication anomalies.
- Actively audit privileged accounts that were recently created or updated.
- Rotate secrets - certificates, keys, and passwords for all connected or exposed systems and applications.
Read details on this vulnerability
Zscaler Zero Trust Exchange Coverage - Zscaler Private Access with Deception Advanced, ITDR, Advanced Cloud Sandbox, Advanced Threat Protection, Advanced Cloud Firewall, SSL Inspection.
European diplomats targeted by SPIKEDWINE with WINELOADER
Our team identified a targeted attack which we dubbed SPIKEDWINE, involving a previously undocumented backdoor called WINELOADER. The attack was discovered through a suspicious PDF masquerading as an invitation from the Ambassador of India. The PDF was sent to European diplomats.
The attack chain (shown in the figure below) involved a multistage process initiated by clicking a malicious link within the PDF invitation. This leads to downloading a ZIP archive containing an HTA file. This HTA file executes obfuscated JavaScript code which in turn downloads and executes the WINELOADER backdoor.
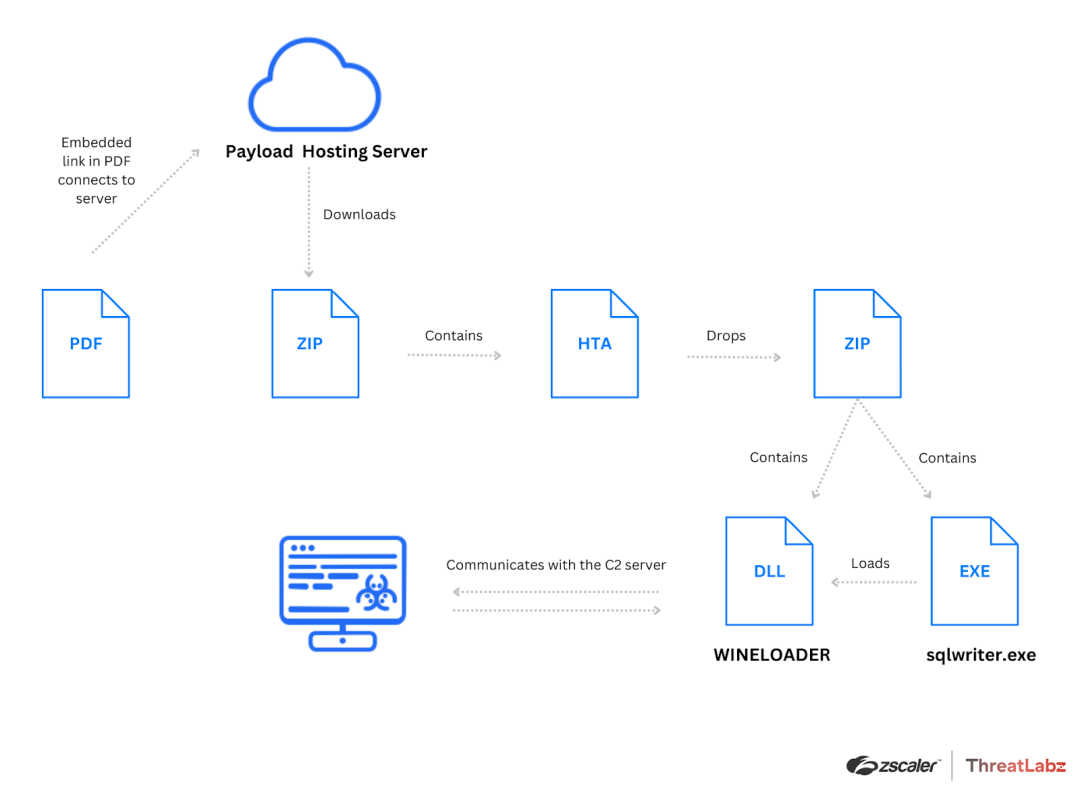
WINELOADER, employs various evasion techniques, injects itself into legitimate system DLLs and communicates with the attacker-controlled C2 server using encrypted HTTP GET requests. The backdoor supports commands such as executing modules from the C2 server, injecting itself into other DLLs, and updating beacon request intervals.
The threat actor leveraged compromised network infrastructure throughout the attack and demonstrated advanced tactics. While we did not attribute these attacks to a specific nation-state actor, the attackers showed a vested interest in exploiting diplomatic relations between India and Europe. Ongoing monitoring is in place to address any new developments associated with this threat.
Zscaler Zero Trust Exchange Coverage - Advanced Cloud Sandbox, Advanced Threat Protection, Advanced Cloud Firewall, SSL Inspection, Browser Isolation.
The (D)Evolution of Pikabot
In our latest technical analysis of Pikabot, a malware loader initially observed in early 2023, we examine the malware’s recent evolution. Following a significant increase in activity after the FBI-led takedown of Qakbot in August 2023, Pikabot ceased activity in December 2023, only to reemerge with substantial changes in February 2024.
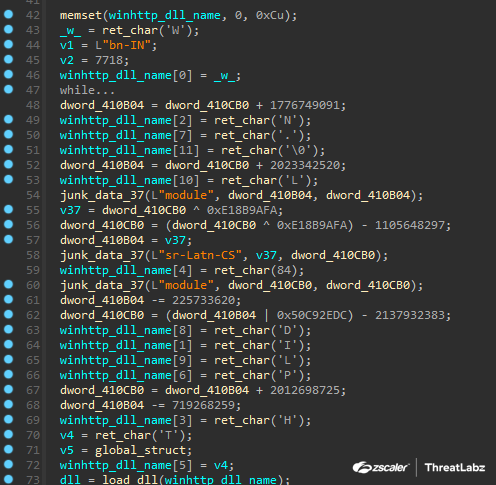
In the latest version of Pikabot, the majority of the strings are either constructed by retrieving each character and pushing it onto the stack. In some rare cases, a few strings are still encrypted using the RC4 algorithm only. Other notable updates include simplification of code, obfuscation techniques, modifications in network communications, and the storage of configuration elements in a single memory block. Technical analysis reveals Pikabot’s utilization of various anti-analysis methods, including string encryption, junk code insertion, and anti-debugging measures. Additionally, Pikabot employs sandbox evasion techniques and language detection to thwart analysis.
Our blog provides insight into Pikabot's bot initialization phase, configuration, and network communications. It highlights the malware’s ongoing development particularly as it relates to evading detection and analysis.
Zscaler Zero Trust Exchange Coverage - Advanced Cloud Sandbox, Advanced Threat Protection, Advanced Cloud Firewall, SSL Inspection, Browser Isolation.
Midnight Blizzard and Active Directory attacks
On January 19 Microsoft disclosed that an advanced cyberattack gave the threat actors access to senior management mailboxes and resulted in sensitive data leakage. The threat actor, identified as Midnight Blizzard, is a state-sponsored Russian threat group. They are also known by the names Nobelium, CozyBear, and APT 29. This threat group was also responsible for a high-profile attack on Hewlett Packard in December 2023, and the infamous SolarWinds attack in 2020.
The attackers targeted Microsoft’s Entra ID environment, gaining access and elevating their privileges via password spraying, exploiting identity, and leveraging SaaS misconfigurations. Once inside, attackers gained unauthorized access to email accounts of Microsoft’s senior leadership team, security team, legal, and others. Midnight Blizzard used several effective tactics and techniques during the attack, including:
- Limiting the number of attack attempts to evade blocking triggered by brute forcing heuristics
- Guessing the right password to compromise the test tenant’s account
- Generating a new secret key for the Test App that allowed the threat actor to control the app everywhere it was installed
- Using the app’s permissions to create an admin user in the corporate tenant
- Using the new admin account to create malicious OAuth apps.
- Granting the malicious app the privilege to impersonate the users of the Exchange service
- Using the malicious app to access Microsoft employee email accounts.
While there is a plethora of known Active Directory (AD) misconfigurations that are exploited in the wild, certain issues occur more commonly than others. Here are top 3 AD issues that we see threat actors actively exploiting in the wild:
- Kerberoastable accounts - Kerberoasting allows regular domain users to obtain Kerberos password hashes for accounts with a ServicePrinicpalName (SPN) attribute set within the user object. These hashes can be cracked offline, with successful cracking dependent on password strength. Adversaries often target regular as well as privileged accounts including Service Accounts using this technique to obtain escalated privileges in the victim environment.
- SubjectAltName certificate extension - AD CS-related attacks are relatively recent and have received less awareness compared to other well-known issues. Misconfigured certificate templates can serve as a means to escalate privileges within the environment, potentially leading to domain user to domain admin compromise.
- Weak permissions - Delegations are utilized to grant specific controls to domain objects without the need to add the object to privileged groups like domain admins. However, misconfigured ACLs can introduce issues that are difficult to identify and can be exploited by adversaries. It is possible for unprivileged accounts to possess control permissions over privileged domain objects such as users, computers, GPOs, and certificates. Depending on the privileges and the object in question, various attack scenarios can be leveraged by an adversary.
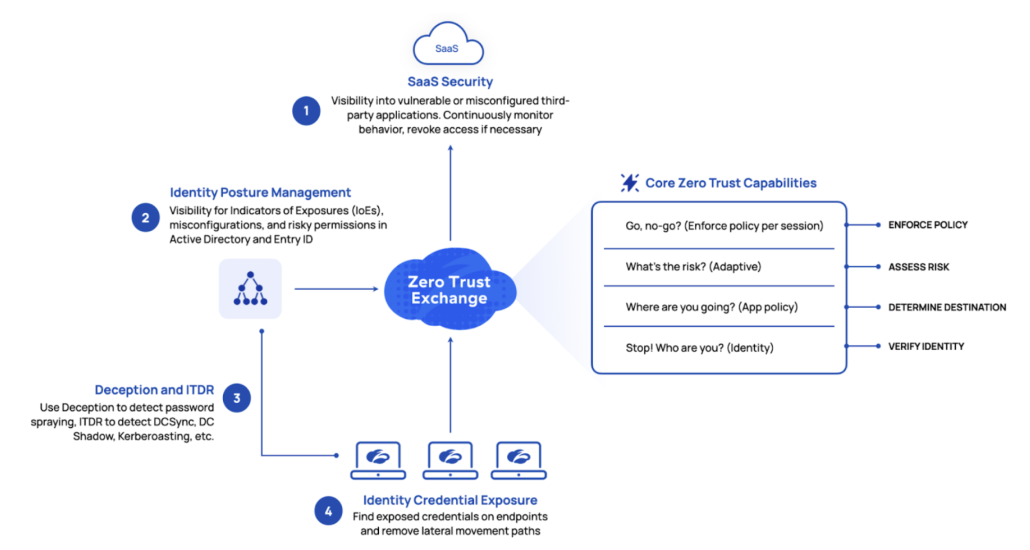
Microsoft’s has issued official guidance for dealing with these attacks. They suggest organizations defend against malicious OAuth applications and audit privileged identities and apps. They also encourage analysts to identify malicious OAuth apps and implement conditional access app control for unmanaged devices. Zscaler customers are protected from Midnight Blizzard attacks on multiple levels due to our cloud-native zero trust architecture. Read our blog for a complete breakdown of these attacks and recommendations for protecting your organization.
Zscaler Zero Trust Exchange Coverage - Zscaler Private Access with Deception Advanced, ITDR, Advanced Cloud Sandbox, Advanced Threat Protection, Advanced Cloud Firewall, SSL Inspection.
About ThreatLabz
ThreatLabz is the embedded research team at Zscaler. This global team includes security experts, researchers, and network engineers responsible for analyzing and eliminating threats across the Zscaler security cloud and investigating the global threat landscape. The team shares its research and cloud data with the industry at large to help promote a safer internet.
The Zscaler Zero Trust Exchange
Zscaler manages the world’s largest security cloud. Each day, Zscaler blocks over 150 million threats to its 7300+ customers, securing over 300 billion web transactions daily. The Zscaler ThreatLabz security research team uses state-of-the-art AI/ML and machine-learning technology to analyze Zscaler Zero Trust Exchange traffic and share its findings.
What to read next:
Threats to water: the Achilles’ heel of critical infrastructure
From gatekeeper to guardian: Why CISOs must embrace their inner business superhero
The CISO's guide to AI: Embracing innovation while mitigating risk
Recommended
