
Aug 15, 2024
Initiative maps Zscaler products, engines, and controls to the scoring rubric from the Center for Threat-Informed Defense, a non-profit, operated by MITRE Engenuity
Here’s a burning question I proposed to an audience I was presenting to at the recent Zenith Live ‘24 conference:
Why does everybody seem to support threat-centric security conceptually, but few practice it operationally?
To address this challenge, I joined a cross-functional team to pilot the “Zscaler MITRE ATT&CK MAPPING Program,” which maps Zscaler products, engines, controls, etc., against the scoring rubric from the Center for Threat-Informed Defense, a non-profit, operated by MITRE Engenuity. With a healthy dose of creative conflict and dialectical decision-making, we set out to become experts in choice architecture, or the design of different ways in which choices and their impacts can be presented to decision makers like you. We did this because there are trade-offs in every cybersecurity decision.
We mulled over the realities of the status quo in cybersecurity. As an industry, we are getting better, but we’re still stuck in this same cyclonic confluence of unmitigated risk and tactical reactivity by necessity.
Accepting responsibility for change is a noble cause, but is challenging and slow-going. Regardless, we chartered a path armed with a mission and design goal I’ve been championing for years: “No material or significant event that would impact my shareholders, stakeholders or my customers, and doing that with the lowest cost and least amount of friction.”
In this article, you'll learn how you can ATT&CK (i.e., manage) risk and strengthen your security posture using a threat-centric mindset. The starting point, as you may have guessed, is zero trust architecture. Implementing effective zero trust strategies requires deep visibility and a comprehensive understanding of real-world attack scenarios. This is where the MITRE ATT&CK framework comes into play.
MITRE ATT&CK + Zscaler ZTE
MITRE ATT&CK helped us first map attack paths and understand the exploitable pivot points that start with an initial foothold or point of compromise through to the catastrophe that causes material impact to our organizations and our customers. Below is the framework showing attack paths by the hacking group Lapsus$ as an example.

Next, we used the Zscaler control-specific MITRE ATT&CK sets of tactics, techniques, and procedures (TTPs) to map product-specific navigator layers, compare threat models, map other frameworks, and find insights into risk hunting and cyber capital planning. We will cover these topics in more detail in future articles and papers.
The result was a total of 1,140 control records covering 451 unique TTPs.

We looked at the TTPs in a given threat model and calculated the total number of paths that an attacker could use to go from left to right through the MITRE ATT&CK chain. We discovered bottlenecks or potential chokepoints, indicating where, for instance, it may be best to start addressing tactics to prevent the initial compromise.
One key output was the MITRE ATT&CK framework to the cyber kill chain to the Zscaler attack anatomy. Bringing these three concepts into alignment can help a CISO better understand where solution coverage is good, where gaps exist, and what should be the next focus area.

Shifting to a proactive, threat-centric mindset
The charting exercises described above gave us unexpected ideas and paths that could yield optimizations for security operations. The value we all saw was how it can help shift thinking from incident reaction to proactive cyber risk management.
To illustrate this point, in the diagram below, the left side represents where almost all the focus resides today—reactive threat hunting and fixation on managing vulnerabilities.
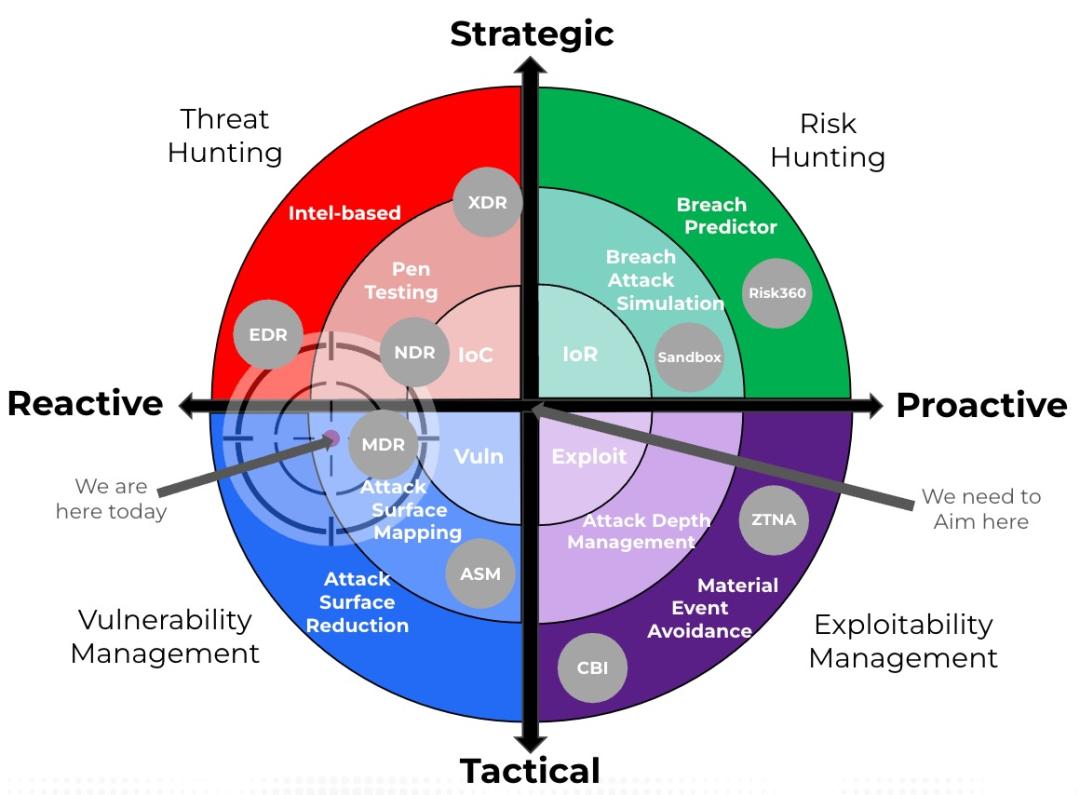
On the vertical axis, we can categorize our work from tactical to strategic. Strategic activities involve the identification of your organization’s long-term interests and the means of achieving them. The horizontal axis defines a continuum of work from reactive to proactive.
Proactive means you are creating or controlling a situation by causing something to happen rather than responding to it after it has happened. Being proactive by almost every implication would lower risks and lower costs, especially if we have zero-trust enabled rich contextual attributes (devices, identities, applications, network segments) within your enterprise to minimize reachability, thereby breaking attack paths before an event occurs.
Risk hunting, managing attack depth, avoiding material events are proactive and is where real economic value lies.
A threat-informed zero trust journey
There are several benefits for pursuing a threat-centric approach.
First, you can prioritize security investments and focus on defending against the most relevant and imminent threats. Second, you can improve your threat detection capabilities by aligning your security capabilities and analytics with known TTPs that are most common in your industry, region, and organization's profile. Third, you can minimize the volume of your incident responses while boosting the effectiveness when you do have to deal with them by having a clear understanding of how attackers operate and the impact of their actions on the organization.
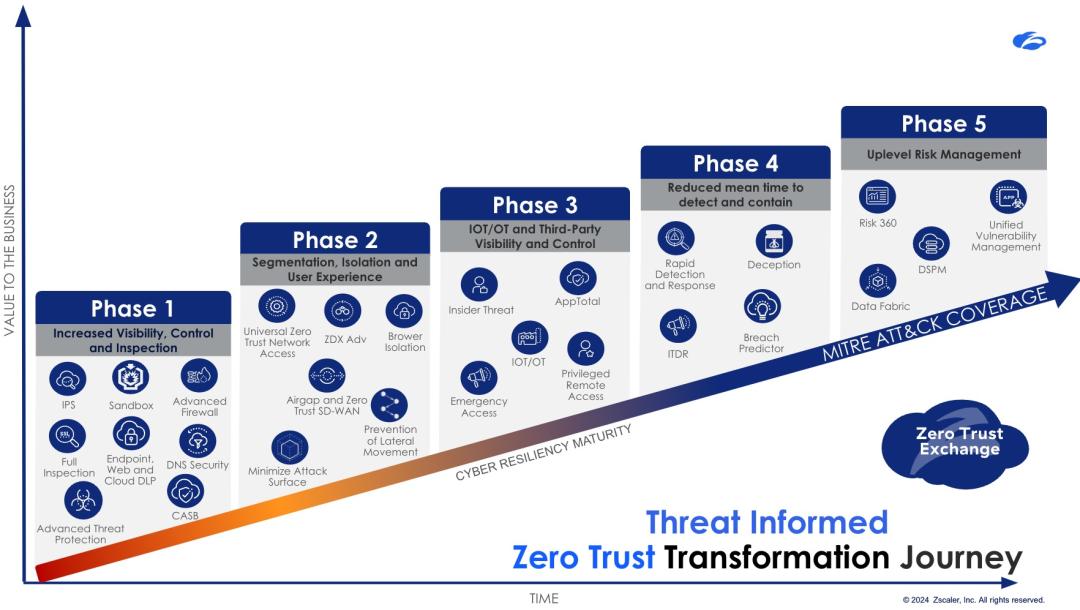
To see where you are and where you want to be, think about which skills and abilities you have now in the five stages below.
What's next
The Zscaler MITRE ATT&CK MAPPING Program can serve as a valuable resource for threat modeling exercises, as we continue work on a comprehensive understanding of the tactics and techniques used by the adversaries that pose a constant danger to our enterprise customers. The team is now mapping Zscaler's capabilities to other frameworks and standards, like the NIST Cybersecurity Framework and ISO 27001. This will help the ecosystem work together better and give more information to both internal and external stakeholders.
Follow Zscaler ThreatLabz for regular insights on the latest ransomware threats and developments, including published indicators of compromise (IOCs) and MITRE ATT&CK mappings. This information can be used to train your team, improve your security posture, and help prevent ransomware attacks.
Contact us to learn more about Zscaler coverage across the MITRE ATT&CK framework, including a custom workshop.
What to read next
Transforming Cybersecurity Response with Zscaler™ using the MITRE ATT&CK™ Framework (2021)
Recommended
