/ What Is Secure Remote Access?
What Is Secure Remote Access?
Secure remote access is an umbrella term that refers to the security measures, policies, and technologies organizations use to deliver network, device, and application access from a location outside of the corporate office with a high level of security.
How Does It Work?
Secure remote access allows employees who are away from the office to use the resources they need to be productive. It provides a means for them to connect to a data center, network, applications, or cloud resources via their remote devices through unsecured home or public Wi-Fi internet connections rather than a corporate network.
Secure remote access gives today’s hybrid employees a buffer that sits between their endpoint and the internet, enabling them to establish remote connections while minimizing the risk of unauthorized access.
Secure remote access technologies and policies vary company to company, as each IT department has its own installations, requirements, and budget for providing secure access from anywhere.
Why Is Secure Remote Access Important?
Today, many businesses are hiring based on qualification rather than location. Remote and hybrid work are here to stay, and with cyberthreat evolution and vulnerabilities both at all-time highs, secure remote access has moved to the top of priority lists for IT and security departments around the world, regardless of industry.
In the past, an organization’s employees were on its network, and all applications resided in the data center connected to that same network. But with the onset of the COVID-19 pandemic, companies were forced to rapidly shift to remote work to stay productive and profitable. This meant adopting remote access solutions to provide users the ability to access internal applications like Microsoft 365 by extending them to the remote user, whether via the network or other methods.
Today’s security standards are drastically different from what they were even five years ago, and the paradigm surrounding secure remote access technologies is shifting quickly.
According to the 2022 VPN Risk Report by Cybersecurity Insiders, more than 80% of surveyed companies plan to implement a zero trust model.
Which Technologies Are Used for Secure Remote Access?
There’s a wide variety of remote access solutions on the market. Let’s look at some of the ones today’s organizations most commonly use.
Virtual Private Network (VPN)
This is the grandfather of all secure remote access solutions. A VPN provides access to a company’s corporate network through a tunnel that sits between the network and a remote user. Once authenticated, users have unrestricted network access and can move laterally about the network.
Two-Factor/Multifactor Authentication (2FA/MFA)
Through this method, a user gains access to a corporate network or resources by authenticating by at least two means. This can be any combination of a password, email address, remote desktop, mobile device, or even biometrics such as a fingerprint. If a user can’t authenticate on both or all fronts, the request is denied.
Single Sign-On (SSO)
SSO allows a user to access any and all resources through one form of authentication, hence “single.” It’s often used by companies of all sizes as well as individuals to avoid having to manage various usernames and passwords.
Privileged Access Management (PAM)
PAM refers to the conjoining of people, processes, and technology to manage access. It gives IT greater visibility into accounts by monitoring them in real time while stopping cyberattacks and insider threats, optimizing operational efficiency, and ensuring compliance. With PAM, users are given access to only the resources they’re authorized to, and access management is much tighter.
Benefits of Secure Remote Access
Secure remote access solutions are worthy assets to your organization, helping you to:
- Keep sensitive data secure. Protect your organization’s data by limiting access from outside sources and only granting it by a secure, controlled means. This greatly reduces your organization’s risk profile, which is crucial given the litany of advanced threats that exist today.
- Reduce the attack surface. Defend even more effectively against advanced threats by reducing the number of attack vectors cybercriminals can use to infiltrate remote endpoints. This helps improve your organization’s security posture.
- Achieve and maintain compliance. Help your organization avoid noncompliance in today’s growing landscape of data protection and privacy regulations by preventing data leaks and data loss.
The Changing Tides
For a few decades now, IT professionals have relied on VPNs to deliver secure remote access. This practice remained even as more and more users began working off the network and accessing corporate resources through their laptops or mobile devices and as more applications and infrastructure moved to the cloud.
Eventually, IT and security departments had to ask themselves a difficult question: With so many users off the network and so many applications in the cloud, does it even make sense to connect remote users to the internal network?
Tethering security to the network is the crux of the issues with the old model for remote access. In addition to higher latency, organizations relying on legacy VPN technology face increased risk in two key areas:
- Inherent, often excessive trust
- Increased risk of external network access
Unlike a zero trust approach, the old castle-and-moat architectures, which rely heavily on VPN, often trust too readily. This flawed philosophy creates a “flat” network that depends on IP-addresses, endpoint-based access controls, and other factors to determine authentication within a corporate network. Once a user is in one of these flat networks, the user can move around the entire corporate network.
This allows bad actors to exploit the VPN attack surface to infiltrate the network and launch ransomware, phishing attacks, denial of service, and other means of exfiltrating critical business data.
In contrast, the zero trust approach treats all traffic, including traffic already inside the perimeter, as hostile. Unless workloads have been identified by a set of context-based attributes, they are untrusted and blocked from communicating.
As we explore below, secure remote access has evolved to meet today’s cloud-first world's demands.
Redefining Secure Remote Access with Zero Trust Network Access
In response to today’s needs, IT teams are leveraging the zero trust network access (ZTNA) framework (also known as software-defined perimeter [SDP])to enable secure remote access for off-network users. ZTNA provides secure access to your private enterprise applications whether they’re hosted in public clouds, private clouds, or your data center, without the need for a VPN.
ZTNA is based on an adaptive trust model, where trust is never implicit, and access is granted on a need-to-know, least-privileged basis defined by granular security policies. These security solutions require no physical appliances and can be deployed in any environment to support all REST API applications.
To be considered ZTNA, a solution must adhere to these four tenets:
- ZTNA isolates the act of providing application access from network access. This reduces risk to your network, such as infection by compromised devices, and only grants application access for authorized users.
- Inside-out connections from app to user ensure that both network and application infrastructure are made invisible to unauthorized users. IPs are never exposed to the internet, creating a “darknet” and making the network impossible to find.
- Application segmentation ensures that once users are authorized, application access is granted on a one-to-one basis so that authorized users have access only to specific applications rather than full access to the network.
- ZTNA takes a user-to-application approach rather than a network-centric approach to security. The network becomes deemphasized, and the internet becomes the new corporate network, leveraging end-to-end encrypted TLS microtunnels instead of MPLS.
Why ZTNA Is More Effective than VPN for Secure Remote Access
When it comes to secure remote access, digital transformation has changed everything. As noted above, VPNs are no longer adequate for keeping up with today’s advanced threats and the volume of users connecting to private applications off-network. This can lead to some serious headaches when it comes to user experiences, connectivity, security, and management.
ZTNA, on the other hand, delivers a better experience for remote workers. There’s no need to log in to a cumbersome VPN. Instead, access is continuous regardless of changes to network connectivity. Plus, ZTNA reduces access latency for faster experiences—regardless of location.
What’s more, ZTNA improves your security posture by moving away from network security and instead focusing on securing the connection between user and application. Access is granted on a one-to-one basis, allowing only authorized users to access specific applications. Lateral movement is impossible, and the attack surface is reduced. Networks and applications are cloaked to unauthorized users, and IPs are never exposed, reducing the threat of internet-based attacks.
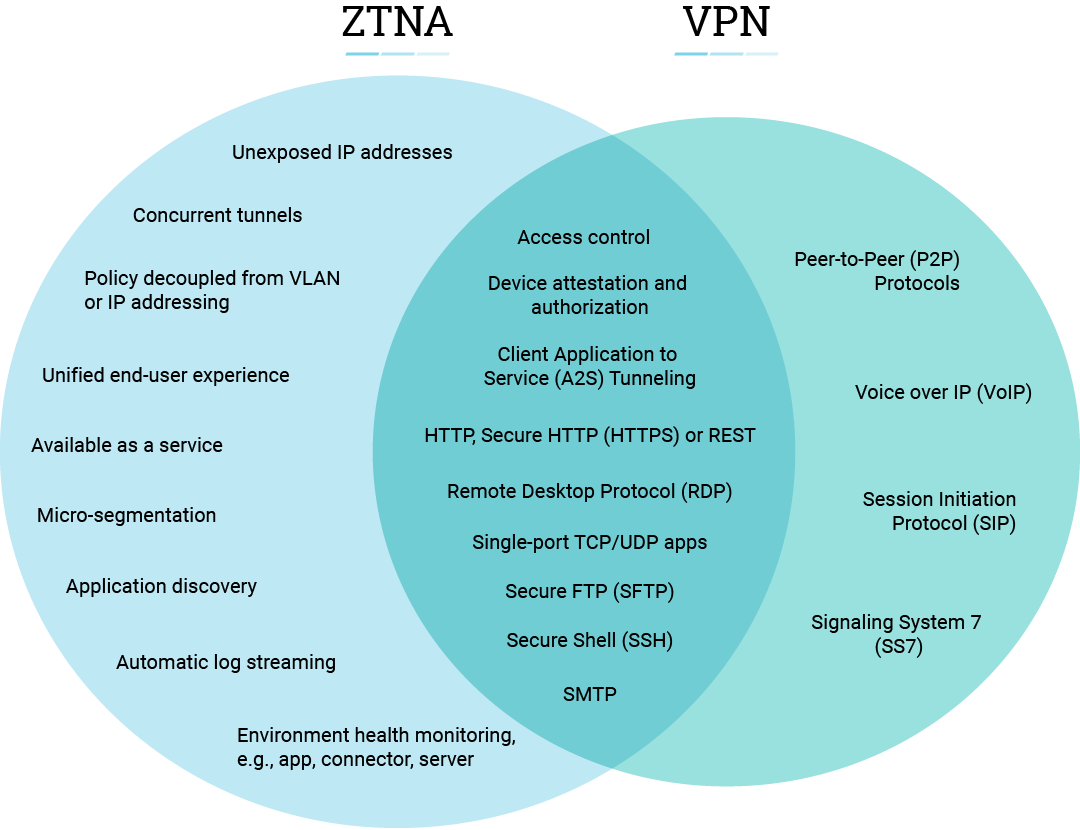
Unlike VPN, ZTNA tools are effortless to manage. This is because with ZTNA, there’s no need to install, configure, and manage appliances. It’s not IP address-centric, so there’s no need to manage ACLs, firewall policies, or translations. Moreover, granular policies can be applied at the application and user level, enabling hyperfocused security to applications and least-privileged access to users.
Choosing a Secure Remote Access Service for Today’s Needs
Although ZTNA solutions are all based on the idea of adaptive trust, ZTNA is available in two forms: ZTNA as a standalone offering and ZTNA as a service.
ZTNA as a standalone offering requires you to deploy and manage all elements of the product. In addition, several IaaS cloud providers offer ZTNA capabilities for their customers. The ZTNA solution sits at the edge of your environment, whether that’s in the data center or cloud, and brokers a secure connection between user and application.
Here are some of the benefits of standalone ZTNA:
- You have direct control and management of the ZTNA infrastructure, which may be required for compliance needs
- IoT services that are hosted on-premises can benefit from optimized speeds
- Performance speeds can increase if local users don’t have to connect out to the internet to access apps hosted on-premises
Standalone ZTNA gives you more control over your environment, but it may be missing out on the benefits of a cloud-delivered service.
Zscaler and ZTNA
The other option is ZTNA as a service, such as Zscaler Private Access™ (ZPA). This is a cloud-hosted service, where you leverage a vendor’s cloud infrastructure for policy enforcement. Your organization simply purchases user licenses and deploys lightweight connectors that front-end applications in all environments, and the vendor delivers the connectivity, capacity, and infrastructure you need.
Access is established through brokered inside-out connections between user and application, effectively decoupling application access from network access while never exposing IP addresses to the internet.
Zscaler Private Access provides myriad organizational benefits, such as:
- Easier deployment since there’s no need to deploy ZTNA gateways
- Simplified management since services are not hosted on-premises
- Optimal pathway always selected for global coverage for a remote workforce
How ZPA Meets Today’s Secure Remote Access Challenges
ZPA provides secure remote access to internal applications in the cloud without placing users on the corporate network. The cloud service requires no complex remote access VPN gateway appliances and uses cloud-hosted policies to authenticate access and route user traffic to the closest application location to them.
ZPA is a software-defined solution that can work in conjunction with direct access technology. It directly connects customer data centers with cloud service provider data centers through the Zscaler Zero Trust Exchange.



